公司在國內、日本、美國、德國、新加坡等多地均有業務,中間業務網絡用的公司專有GPN(Global Private Network中文名是全球私有化網絡)鏈路,目前測試搭建一條備用鏈路,用於網絡冗餘和故障切換。
初步選用方案GRE over IPSec,跑ospf路由協議。
一、爲何要選GRE over IPSec:
各個site網絡比較多,需要使用路由協議進行互聯;
IPSEC不支持組播,即不能傳遞路由協議,在承載路由協議上不如GRE隧道方便;
GRE隧道不能提供加密保障;
使用GRE在兩個網關之間搭建一個隧道,運行路由協議及傳輸正常數據,使用IPSec對整個GRE隧道進行加密,因此需要把兩者進行結合。
二、測試環境:
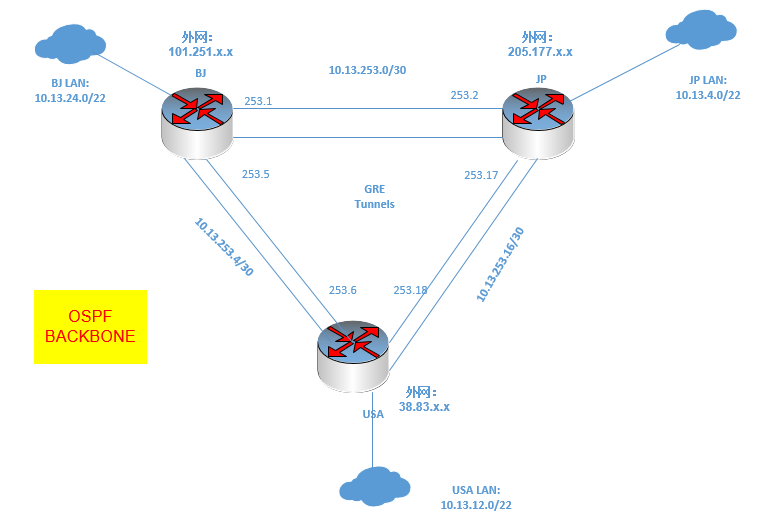
以中國、日本、美國三地爲例,基本網絡拓撲如下圖,用Mikrotik RouterOS(簡稱ROS)做路由器和防火牆,中間跑ospf協議。GPN鏈路就相當於一個大二層,能夠把中日美三地打通,相當於專線,因此在網絡質量上優於直接走大網,做業務主線,這裏不多寫;主要寫一下如何配置GRE鏈路實現備用鏈路功能,在GPN鏈路中斷的時候能夠自動切換到備線。
routeros上配置外網:
中國:101.251.x.x
日本:205.177.x.x
美國:38.83.x.x
三地的內網地址:
中國:10.13.24.0/22
日本:10.13.4.0/22
美國:10.13.12.0/22
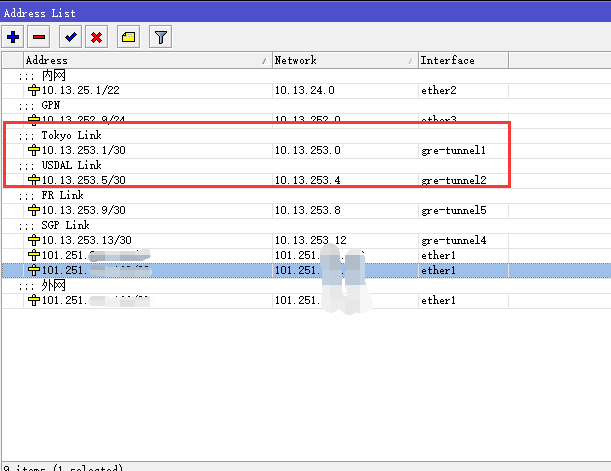
三地互聯地址(用10.13.253.0/24段做互聯地址段):
中國和日本:10.13.253.0/30
日本和美國:10.13.253.16/30
美國和中國:10.13.253.4/30
GPN鏈路網段:
10.13.252.0/24
三、配置
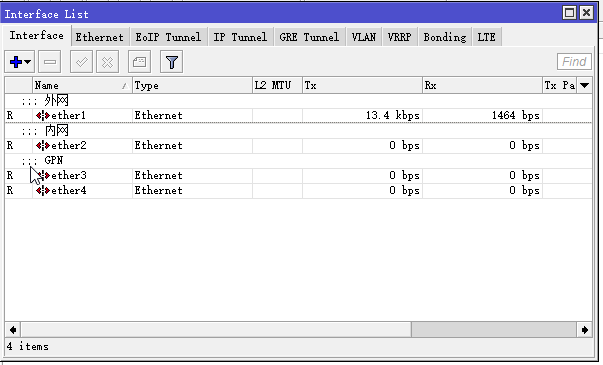
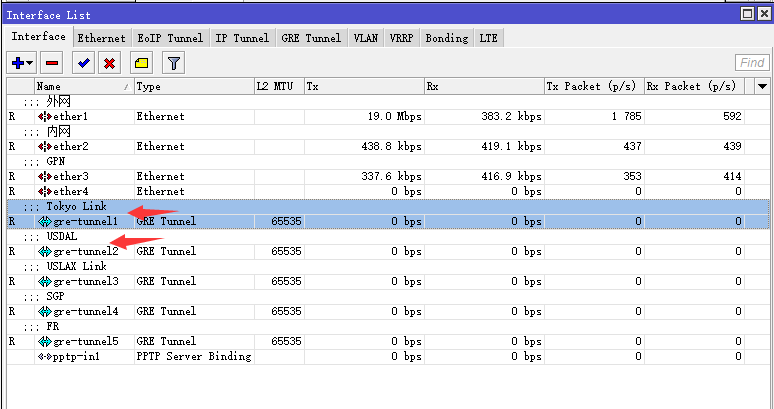
1、三個ros的interface(ether1/2/3分別對應着外網/內網/GPN網絡):
2、IPSec配置
中國:
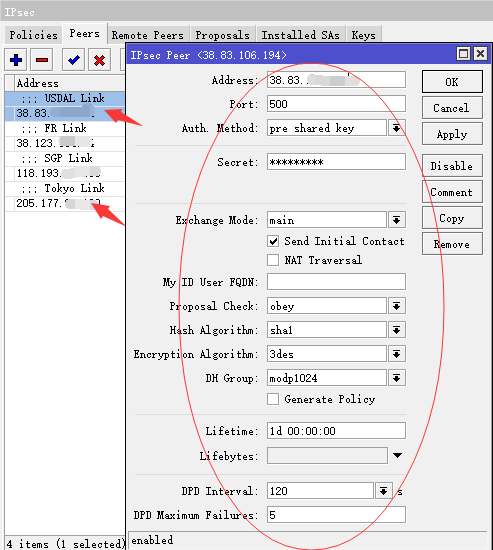
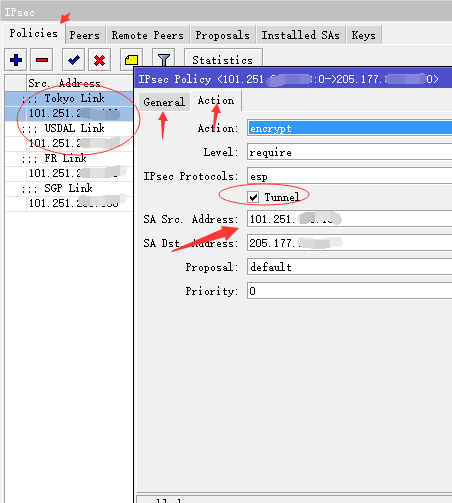
/ip ipsec peer add address=205.177.x.x/32:500 comment="JP Link" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 add address=38.83.x.x/32:500 comment= "USALink" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 /ip ipsec policy add src-address=101.251.x.x/32:any dst-address=205.177.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=101.251.x.x sa-dst-address=205.177.x.x proposal=default priority=0 add src-address=101.251.x.x/32:any dst-address=38.83.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=101.251.x.x sa-dst-address=38.83.x.x proposal=default priority=0
日本:
/ip ipsec peer add address=101.251.x.x/32:500 comment="BJ Link" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 add address=38.83.x.x/32:500 comment= "USA Link" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 /ip ipsec policy add src-address=205.177.x.x/32:any dst-address=101.251.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=205.177.x.x sa-dst-address=101.251.x.x proposal=default priority=0 add src-address=205.177.x.x/32:any dst-address=38.83.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=205.177.x.x sa-dst-address=38.83.x.x proposal=default priority=0
美國:
/ip ipsec peer add address=101.251.x.x/32:500 comment="BJ Link" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 add address=205.177.x.x/32:500 comment= "JP Link" auth-method=pre-shared-key secret="mypassword" generate-policy=no exchange-mode=main send-initial-contact=yes nat-traversal=no proposal-check=obey hash-algorithm=sha1 enc-algorithm=3des dh-group=modp1024 lifetime=1d lifebytes=0 dpd-interval=disable-dpd dpd-maximum-failures=5 /ip ipsec policy add src-address=38.83.x.x/32:any dst-address=101.251.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=38.83.x.x sa-dst-address=101.251.x.x proposal=default priority=0 add src-address=38.83.x.x/32:any dst-address=205.177.x.x/32:any protocol=all action=encrypt level=require ipsec-protocols=esp tunnel=yes sa-src-address=38.83.x.x sa-dst-address=205.177.x.x proposal=default priority=0
中國示例圖:
3、GRE配置:
中國:
/interface gre add name= gre-tunnel1 local-address=101.251.x.x remote-address=205.177.x.x comment="JP Link" add name= gre-tunnel2 local-address=101.251.x.x remote-address=38.83.x.x comment="USA Link" /ip address add address=10.13.253.1/30 interface=gre-tunnel1 network=10.13.253.0 comment="JP Link" add address=10.13.253.5/30 interface=gre-tunnel2 network=10.13.253.4 comment="USA Link"
日本:
/interface gre add name= gre-tunnel1 local-address=205.177.x.x remote-address=101.251.x.x comment="BJ Link" add name= gre-tunnel2 local-address=101.251.x.x remote-address=38.83.x.x comment="USA Link" /ip address add address=10.13.253.2/30 interface=gre-tunnel1 network=10.13.253.0 comment="BJ Link" add address=10.13.253.17/30 interface=gre-tunnel2 network=10.13.253.16 comment="USA Link"
美國:
/interface gre add name= gre-tunnel1 local-address=38.83.x.x remote-address=101.251.x.x comment="BJ Link" add name= gre-tunnel2 local-address=38.83.x.x remote-address=205.177.x.x comment="JP Link" /ip address add address=10.13.253.6/30 interface=gre-tunnel1 network=10.13.253.4 comment="BJ Link" add address=10.13.253.18/30 interface=gre-tunnel2 network=10.13.253.16 comment="JP Link"
中國示例圖:
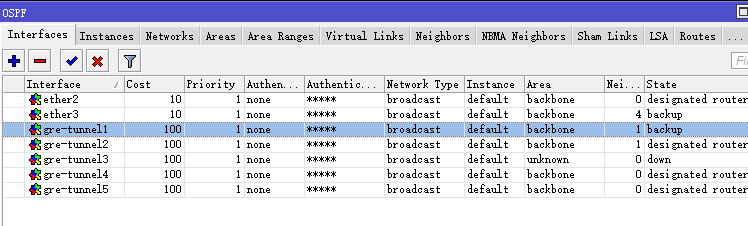
4、OSPF配置
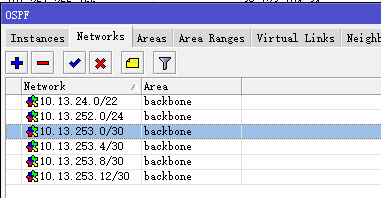
把本地的內網地址段、GPN網段(10.13.252.0/24),GRE互聯地址網段都宣佈進去,cost值GPN鏈路的優先級高,設爲10,GRE Tunnel的cost值設爲100:
中國:
/routing ospf> interface add interface=eth2 cost=10 interface add interface=eth3 cost=10 interface add interface=gre-tunnel1 cost=100 interface add interface=gre-tunnel2 cost=100 /routing ospf> network add network=10.13.24.0/22 area=backbone comment="內網" network add network=10.13.252.0/24 area=backbone comment="GPN" network add network=10.13.253.0/30 area=backbone comment="JP Link" network add network=10.13.253.4/30 area=backbone comment="USA Link"
日本:
/routing ospf> interface add interface=eth2 cost=10 interface add interface=eth3 cost=10 interface add interface=gre-tunnel1 cost=100 interface add interface=gre-tunnel2 cost=100 /routing ospf> network add network=10.13.4.0/22 area=backbone comment="內網" network add network=10.13.252.0/24 area=backbone comment="GPN" network add network=10.13.253.0/30 area=backbone comment="BJ Link" network add network=10.13.253.16/30 area=backbone comment="USA Link"
美國:
/routing ospf> interface add interface=eth2 cost=10 interface add interface=eth3 cost=10 interface add interface=gre-tunnel1 cost=100 interface add interface=gre-tunnel2 cost=100 /routing ospf> network add network=10.13.12.0/22 area=backbone comment="內網" network add network=10.13.252.0/24 area=backbone comment="GPN" network add network=10.13.253.4/30 area=backbone comment="BJ Link" network add network=10.13.253.16/30 area=backbone comment="JP Link"
北京示例圖:
四、驗證
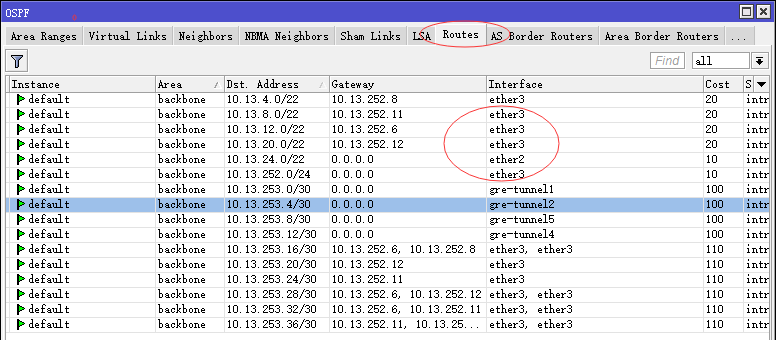
1、查看ospf是否啓動成功:
2、down掉GPN的interface,查看ospf的路由是否自動切換到GRE Tunnel:
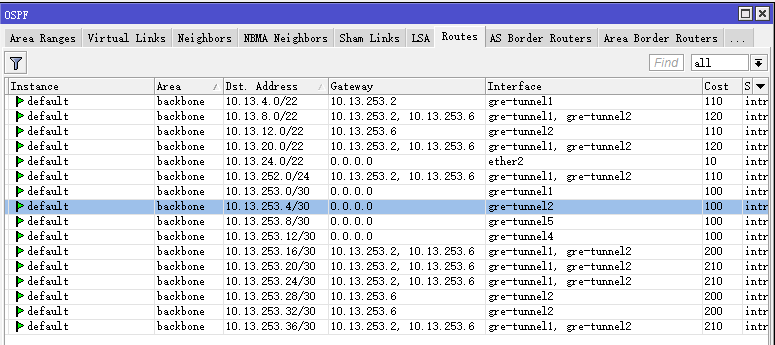
success!
五、優化
此文中只選了3個site,備線的ospf cost值均設爲了100,;在實際部署時會多於3個,ospf值的設置,可以設置爲點對點的延遲值,使在切換到備線時ospf選路選的是線路延遲最低的路徑,也是最優的路徑。比如中日之間大網延遲大概爲55ms,可以把GRE的ospf cost設爲55。