在Node節點部署組件
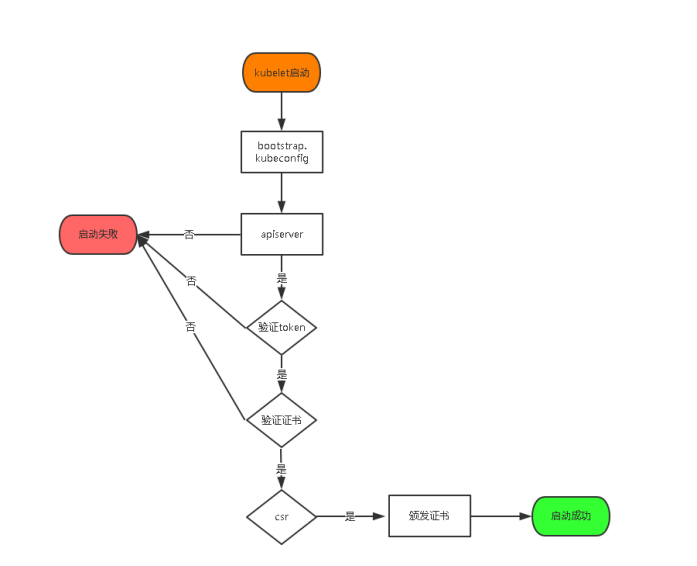
Master apiserver啓用TLS認證後,Node節點kubelet組件想要加入集羣,必須使用CA簽發的有效證書才能與
apiserver通信,當Node節點很多時,簽署證書是一件很繁瑣的事情,因此有了TLS Bootstrapping機制,kubelet
會以一個低權限用戶自動向apiserver申請證書,kubelet的證書由apiserver動態簽署。
認證大致工作流程如圖所示:
1、將kubelet-bootstrap用戶綁定到系統集羣角色
在主節點(192.168.1.13)上運行
[root@docker kubeconfig]# kubectl create clusterrolebinding kubelet-bootstrap \
--clusterrole=system:node-bootstrapper \
--user=kubelet-bootstrap
返回結果:
clusterrolebinding.rbac.authorization.k8s.io/kubelet-bootstrap created
2、拷貝文件:(將前面下載的二進制包中的kubelet和kube-proxy拷貝到/opt/kubernetes/bin目錄下)
[root@docker bin]# pwd
/data/tools/k8s/kubernetes/server/bin
[root@docker bin]# scp kubelet kube-proxy 192.168.1.23:/opt/kubernetes/bin/
[root@docker bin]# scp kubelet kube-proxy 192.168.1.24:/opt/kubernetes/bin/
執行腳本,生成 kube-proxy.kubeconfig bootstrap.kubeconfig 2個文件
cat /data/k8s/kubeconfig/kubeconfig.sh
[root@docker kubeconfig]# cat kubeconfig.sh
#-----------------start-----------------------------------------------------------------------------------------
#已經創建 cat /opt/kubernetes/cfg/token.csv 就不需要再創建了
#創建 TLS Bootstrapping Token
#BOOTSTRAP_TOKEN=$(head -c 16 /dev/urandom | od -An -t x | tr -d ' ')
#BOOTSTRAP_TOKEN=0fb61c46f8991b718eb38d27b605b008
#cat > token.csv << EOF
#${BOOTSTRAP_TOKEN},kubelet-bootstrap,10001,"system:kubelet-bootstrap"
#EOF
BOOTSTRAP_TOKEN=674c457d4dcf2eefe4920d7dbb6b0ddcc
APISERVER=$1
SSL_DIR=$2
#創建kubelet bootstrapping kubeconfig
export KUBE_APISERVER="https://$APISERVER:6443"
#設置集羣參數
kubectl config set-cluster kubernetes \
--certificate-authority=$SSL_DIR/ca.pem \
--embed-certs=true \
--server=${KUBE_APISERVER} \
--kubeconfig=bootstrap.kubeconfig
#設置客戶端認證參數
kubectl config set-credentials kubelet-bootstrap \
--token=${BOOTSTRAP_TOKEN} \
--kubeconfig=bootstrap.kubeconfig
#設置上下文參數
kubectl config set-context default \
--cluster=kubernetes \
--user=kubelet-bootstrap \
--kubeconfig=bootstrap.kubeconfig
#設置默認上下文
kubectl config use-context default --kubeconfig=bootstrap.kubeconfig
#創建kube-proxy kubeconfig文件
kubectl config set-cluster kubernetes \
--certificate-authority=$SSL_DIR/ca.pem \
--embed-certs=true \
--server=${KUBE_APISERVER} \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-credentials kube-proxy \
--client-certificate=$SSL_DIR/kube-proxy.pem \
--client-key=$SSL_DIR/kube-proxy-key.pem \
--embed-certs=true \
--kubeconfig=kube-proxy.kubeconfig
kubectl config set-context default \
--cluster=kubernetes \
--user=kube-proxy \
--kubeconfig=kube-proxy.kubeconfig
kubectl config use-context default --kubeconfig=kube-proxy.kubeconfig
#-----------------end-----------------------------------------------------------------------------------------
參數1:本地ip,參數2:ca.pem目錄
[root@docker kubeconfig]# bash kubeconfig.sh 192.168.1.13 /data/k8s/master-ca
3、拷貝文件
[root@docker kubeconfig]# scp bootstrap.kubeconfig kube-proxy.kubeconfig 192.168.1.23:/opt/kubernetes/cfg/
[root@docker kubeconfig]# scp bootstrap.kubeconfig kube-proxy.kubeconfig 192.168.1.24:/opt/kubernetes/cfg/
部署kubelet組件
1、創建kubelet配置文件
[root@docker cfg]# cd /opt/kubernetes/cfg
[root@docker cfg]# cat kubelet.sh
#--------------------start-------------------------------------------------------------
#!/bin/bash
NODE_ADDRESS=$1
DNS_SERVER_IP=${2:-"10.0.0.2"}
cat <<EOF >/opt/kubernetes/cfg/kubelet
KUBELET_OPTS="--logtostderr=true \
--v=4 \
--hostname-override=${NODE_ADDRESS} \
--kubeconfig=/opt/kubernetes/cfg/kubelet.kubeconfig \
--bootstrap-kubeconfig=/opt/kubernetes/cfg/bootstrap.kubeconfig \
--config=/opt/kubernetes/cfg/kubelet.config \
--cert-dir=/opt/kubernetes/ssl \
--pod-infra-container-image=registry.cn-hangzhou.aliyuncs.com/google-containers/pause-amd64:3.0"
EOF
cat <<EOF >/opt/kubernetes/cfg/kubelet.config
kind: KubeletConfiguration
apiVersion: kubelet.config.k8s.io/v1beta1
address: ${NODE_ADDRESS}
port: 10250
readOnlyPort: 10255
cgroupDriver: cgroupfs
clusterDNS:
- ${DNS_SERVER_IP}
clusterDomain: cluster.local.
failSwapOn: false
authentication:
anonymous:
enabled: true
EOF
cat << EOF > /usr/lib/systemd/system/kubelet.service
[Unit]
Description=Kubernetes Kubelet
After=docker.service
Requires=docker.service
[Service]
EnvironmentFile=/opt/kubernetes/cfg/kubelet
ExecStart=/opt/kubernetes/bin/kubelet \$KUBELET_OPTS
Restart=on-failure
KillMode=process
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable kubelet
systemctl restart kubelet
#--------------------end-------------------------------------------------------------
執行腳本(生成kubelet、kubelet.config配置文件):
bash kubelet.sh 192.168.1.23
參數說明:
--hostname-override 在集羣中顯示的主機名
--kubeconfig 指定kubeconfig文件位置,會自動生成
--bootstrap-kubeconfig 指定剛纔生成的bootstrap.kubeconfig文件
--cert-dir 頒發證書存放位置
--pod-infra-container-image 管理Pod網絡的鏡像
systemd管理kubelet組件:
[root@docker cfg]# cat /usr/lib/systemd/system/kubelet.service
[Unit]
Description=Kubernetes Kubelet
After=docker.service
Requires=docker.service
[Service]
EnvironmentFile=/opt/kubernetes/cfg/kubelet
ExecStart=/opt/kubernetes/bin/kubelet $KUBELET_OPTS
Restart=on-failure
KillMode=process
[Install]
WantedBy=multi-user.target
啓動:
systemctl daemon-reload
systemctl enable kubelet
systemctl restart kubelet
錯誤日誌:/var/log/message
很大一個原因是:在master主機上生成的配置文件(bootstrap.kubeconfig kube-proxy.kubeconfig)有問題,需要在看看
在Master審批Node加入集羣:
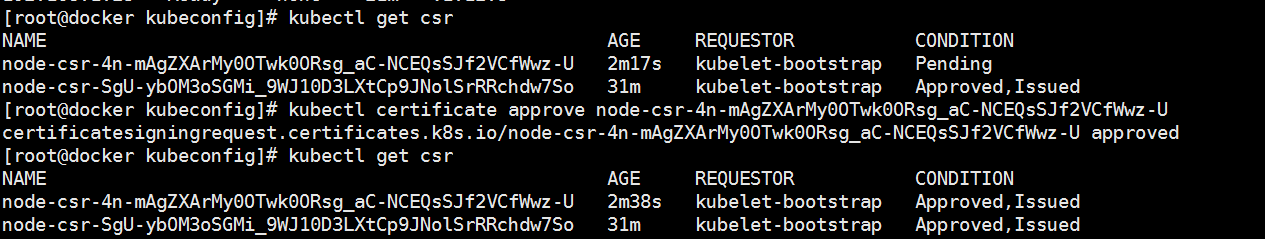
啓動後還沒加入到集羣中,需要手動允許該節點纔可以。 在Master節點查看請求籤名的Node:
主節點上:
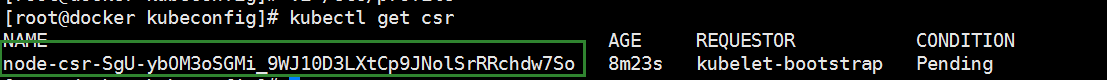
查看未授權的CSR請求:
通過CSR請求:
[root@docker kubeconfig]# kubectl certificate approve node-csr-SgU-ybOM3oSGMi_9WJ10D3LXtCp9JNolSrRRchdw7So
certificatesigningrequest.certificates.k8s.io/node-csr-SgU-ybOM3oSGMi_9WJ10D3LXtCp9JNolSrRRchdw7So approved
驗證:
通過CSR請求:
[root@docker kubeconfig]# kubectl get csr
NAME AGE REQUESTOR CONDITION
node-csr-SgU-ybOM3oSGMi_9WJ10D3LXtCp9JNolSrRRchdw7So 9m48s kubelet-bootstrap Approved,Issued
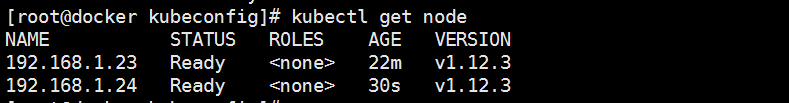
查看node節點
[root@docker kubeconfig]# kubectl get node
NAME STATUS ROLES AGE VERSION
192.168.1.23 NotReady <none> 8s v1.12.3
[root@docker kubeconfig]# kubectl get node
NAME STATUS ROLES AGE VERSION
192.168.1.23 Ready <none> 11s v1.12.3
部署kube-proxy組件
執行腳本(包含創建kube-proxy、啓動項kube-proxy.service):
[root@docker cfg]# cd /opt/kubernetes/cfg
[root@docker cfg]# cat proxy.sh
#-----------------------------start----------------------------------------------------------------
#!/bin/bash
NODE_ADDRESS=$1
cat <<EOF >/opt/kubernetes/cfg/kube-proxy
KUBE_PROXY_OPTS="--logtostderr=true \
--v=4 \
--hostname-override=${NODE_ADDRESS} \
--cluster-cidr=10.0.0.0/24 \
--proxy-mode=ipvs \
--kubeconfig=/opt/kubernetes/cfg/kube-proxy.kubeconfig"
EOF
cat <<EOF >/usr/lib/systemd/system/kube-proxy.service
[Unit]
Description=Kubernetes Proxy
After=network.target
[Service]
EnvironmentFile=-/opt/kubernetes/cfg/kube-proxy
ExecStart=/opt/kubernetes/bin/kube-proxy \$KUBE_PROXY_OPTS
Restart=on-failure
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable kube-proxy
systemctl restart kube-proxy
#-----------------------------end----------------------------------------------------------------
執行腳本:sh proxy.sh 192.168.1.23
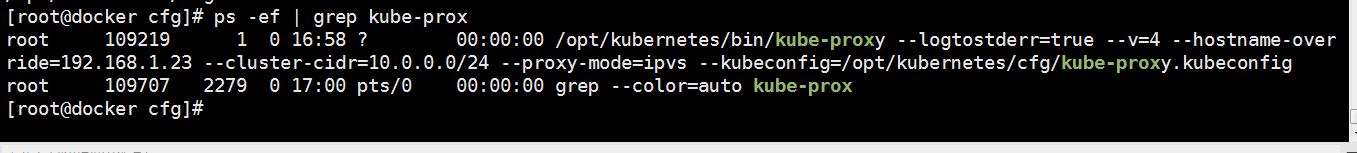
驗證:
查看是否啓動:
部署node2(192.168.1.24)節點
1、拷貝node1(192.168.1.23)上的整個kubernetes 包
scp -r kubernetes/ 192.168.1.24:/opt/
2、scp -r /usr/lib/systemd/system/{kubelet,kube-proxy}.service 192.168.1.24:/usr/lib/systemd/system/
3、到node2上修改IP
cd /opt/kubernetes/cfg
修改kubelet、kubelet.config、kube-proxy爲:192.168.1.24
4、啓動:
systemctl start kubelet
systemctl start kube-proxy
systemctl enable kube-proxy
systemctl enable kubelet
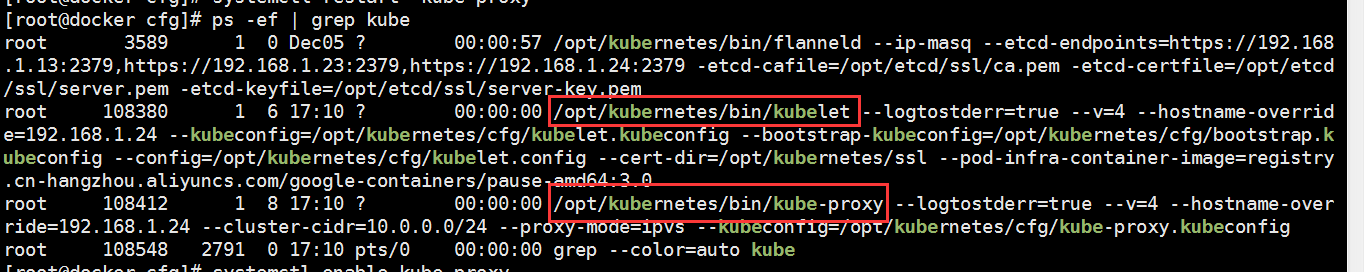
5、驗證
6、加入集羣
單機羣部署總結
部署前所有節點關閉firewalld(systemctl stop firewalld),並同步互聯網時間。
1、自籤ETCD證書
2、ETCD部署
3、Node安裝Docker
4、Flannel部署(先寫入子網到etcd)
5、自籤APIServer證書
6、部署APIServer組件(token.csv)
7、部署controller-manager(指定apiserver證書)和scheduler組件
8、生成kubeconfig(bootstrap.kubeconfig和kube-proxy.kubeconfig)
9、部署kubelet組件(kubectl create clusterrolebinding kubelet-bootstrap ...)
10、部署kube-proxy組件
11、kubectl get csr && kubectl certificate approve 允許頒發證書,加入集羣
12、增加一個Node(刪除第一臺Node已生成的ssl/*證書,修改kubelet,kubele.config,kube-proxy裏Node IP)