Openssl生成證書流程
偶然想到在內網配置https,就梳理了下利用openssl與ca生成證書的過程。
生成過程分爲服務端跟客戶端,這裏我在一臺上測試。
一.介紹
CA是Certificate Authority的縮寫,也就是認證中心。
CA的功能有:頒發證書,更新證書,撤銷證書和驗證證書,相當於公安局的戶籍部門。
CA證書的作用是作身份認證。
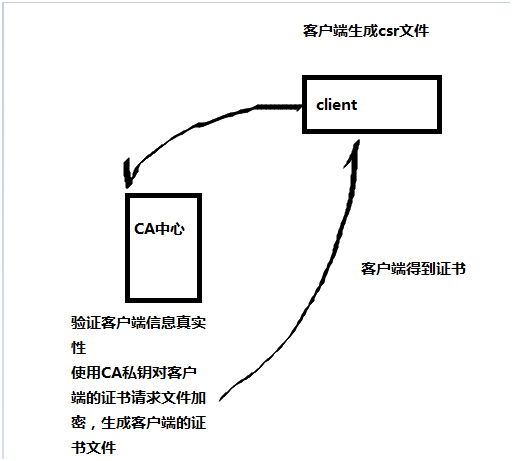
數字證書認證過程:
×××辦理過程: 帶上戶口本-》當地派出所-》簽發證書-》你去領證書
×××辦理過程: 帶上戶口本(證明你合法)-》當地派出所(認證機構)-》簽發證書(審覈有效信息)-》你去領證書。
客戶得到CA證書的流程如下:
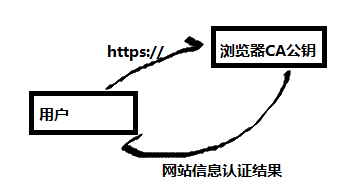
CSR文件根據客戶端的公鑰和主機標識生成,主機標識包括國家,省區,縣市,組織,郵箱,主機名等信息。用戶在拿到數字證書後,用瀏覽器中的CA的公鑰解開證書,得到客戶端的標識,從而確認身份
二.搭建
1.必備軟件openssl,查看是否已安裝
[root@ayu conf]# rpm -qf which openssl
openssl-1.0.1e-48.el6_8.3.x86_64
2.配置自己的CA認證中心。生成CA的根證書和私鑰,根證書包括CA的公鑰
修改openssl配置文件[root@ayu conf]# vim /etc/pki/tls/openssl.cnf
修改如下
#basicConstraints=CA:FALSE
basicConstraints=CA:TRUE設置使用本地爲CA認證中心。
[root@ayu conf]# /etc/pki/tls/misc/CA -h
usage: /etc/pki/tls/misc/CA -newcert|-newreq|-newreq-nodes|-newca|-sign|-verify
選項 :
-newcert 新證書
-newreq 新請求
-newreq-nodes 新請求節點
-newca 新的CA證書
-sign 簽證
-verify 驗證
[root@ayu conf]# /etc/pki/tls/misc/CA -newcert
Generating a 2048 bit RSA private key
.+++
...........................................................................................................................+++
writing new private key to 'newkey.pem'
Enter PEM pass phrase:輸入保護祕鑰文件的密碼
Verifying - Enter PEM pass phrase:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [XX]:CH
State or Province Name (full name) []:hubei
Locality Name (eg, city) [Default City]:wuhan
Organization Name (eg, company) [Default Company Ltd]:ayu
Organizational Unit Name (eg, section) []:ayu
Common Name (eg, your name or your server's hostname) []:ayu
Email Address []:[email protected]
Certificate is in newcert.pem, private key is in newkey.pem
[root@ayu certificate]# ll
總用量 8
-rw-r--r--. 1 root root 1350 3月 20 00:50 newcert.pem
-rw-r--r--. 1 root root 1834 3月 20 00:50 newkey.pem
可以看到已經生成兩個文件,一個爲根證書(公鑰),一個爲祕鑰。
3.客戶端認證文件準備
[root@ayu certificate_keys]# openssl genrsa -des3 -out server.key
Generating RSA private key, 1024 bit long modulus
.............++++++
................++++++
e is 65537 (0x10001)
Enter pass phrase for server.key:輸入私鑰密碼
Verifying - Enter pass phrase for server.key:
生成客戶端私鑰祕鑰文件,des3是保護私鑰的密碼的加密算法
生成客戶端的認證請求文件
[root@ayu certificate_keys]# openssl req -new -key server.key -out server.csr
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
Country Name (2 letter code) [XX]:CH 這些信息與CA的主機標識相同,否則認證會出錯
State or Province Name (full name) []:hubei
Locality Name (eg, city) [Default City]:wuhan
Organization Name (eg, company) [Default Company Ltd]:ayu
Organizational Unit Name (eg, section) []:ayu
Common Name (eg, your name or your server's hostname) []:ayu
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:不輸入密碼
An optional company name []:不輸入密碼
[root@ayu certificate_keys]# ll
總用量 8
-rw-r--r--. 1 root root 668 3月 20 01:23 server.csr
-rw-r--r--. 1 root root 963 3月 20 01:18 server.key
生成的csr文件即根據私鑰文件生成的包含公鑰的請求文件
4.CA認證請求證書
[root@ayu certificate_keys]# openssl ca -keyfile /root/certificate/newkey.pem -cert /root/certificate/newcert.pem -in server.csr -out server.crt
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /root/certificate/newkey.pem:
/etc/pki/CA/index.txt: No such file or directory
unable to open '/etc/pki/CA/index.txt'
140602402772808:error:02001002:system library:fopen:No such file or directory:bss_file.c:398:fopen('/etc/pki/CA/index.txt','r')
140602402772808:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:400:
出現報錯
此時需要做以下操作
[root@ayu certificate_keys]# touch /etc/pki/CA/index.txt
[root@ayu certificate_keys]# echo 01 > /etc/pki/CA/serial
[root@ayu certificate_keys]# openssl ca -keyfile /root/certificate/newkey.pem -cert /root/certificate/newcert.pem -in server.csr -out server.crt
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for /root/certificate/newkey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Mar 20 05:37:46 2018 GMT
Not After : Mar 20 05:37:46 2019 GMT
Subject:
countryName = CH
stateOrProvinceName = hubei
organizationName = ayu
organizationalUnitName = ayu
commonName = ayu
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
00:4C:C6:86:B4:EF:88:51:FC:DB:59:C7:D8:32:20:08:81:7A:4B:D8
X509v3 Authority Key Identifier:
keyid:8A:41:B4:0B:50:11:DC:27:24:A8:29:E6:3B:5A:D1:AB:66:29:3A:EC
Certificate is to be certified until Mar 20 05:37:46 2019 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@ayu certificate_keys]# ll
總用量 12
-rw-r--r--. 1 root root 3747 3月 20 01:37 server.crt
-rw-r--r--. 1 root root 668 3月 20 01:23 server.csr
-rw-r--r--. 1 root root 963 3月 20 01:18 server.key
創建成功。
測試https配置是否成功
在nginx配置問價加上以下字段
listen 443 ssl;
ssl_certificate /usr/local/nginx/conf/certificate_keys/server.crt;
ssl_certificate_key /usr/local/nginx/conf/certificate_keys/server.key;
重啓nginx,測試訪問: