源碼:
https://github.com/haidragon/SSDTHOOK_win7x64/tree/master/SSDTHOOK_win7x64
SSDT表的查找:
https://blog.csdn.net/zfdyq0/article/details/26515019
補充知識點:
syscall是AMD CPU下的sysenter,以此進入內核層,由於64位下沒有nt!KiFastCallEntry,而改用的是nt!KiSystemCall64,在64位系統下啓用了四個新的MSR寄存器,有不同的作用,其中MSR_LSTAR保存的是rip的相關信息,可以通過rdmsr c0000082的方法查看到syscall跳轉地址。這個地址正是nt!KiSystemCall64的入口地址。
32位與64位call地址的區別見:
逆向工程核心原理 390頁
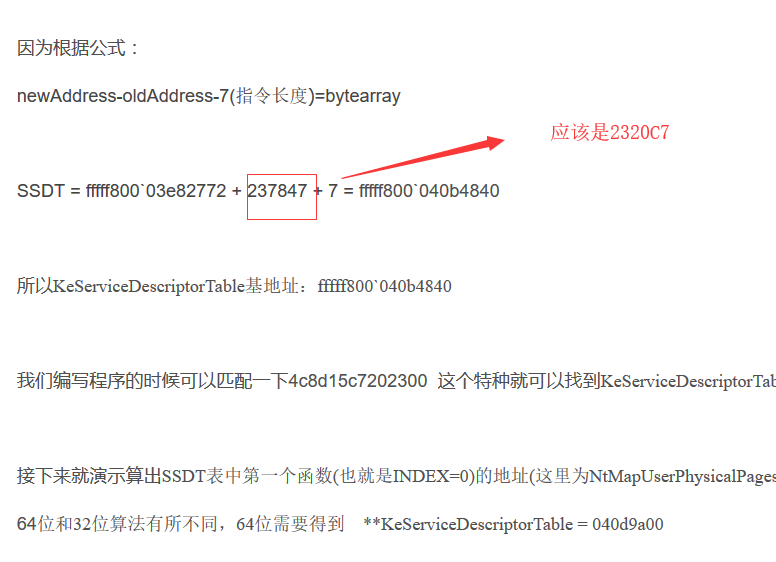
糾正上面博客的一個錯誤:
剛好是fffff800`03e82772 4c8d15c7202300 後面四個字節(002320C7)
4c8d 是lea指令opcode 15表示r10
kd> u KiSystemServiceStart
nt!KiSystemServiceStart:
fffff800`03e8275e 4889a3d8010000 mov qword ptr [rbx+1D8h],rsp
fffff800`03e82765 8bf8 mov edi,eax
fffff800`03e82767 c1ef07 shr edi,7
fffff800`03e8276a 83e720 and edi,20h
fffff800`03e8276d 25ff0f0000 and eax,0FFFh
nt!KiSystemServiceRepeat:
fffff800`03e82772 4c8d15c7202300 lea r10,[nt!KeServiceDescriptorTable (fffff800`040b4840)]
fffff800`03e82779 4c8d1d00212300 lea r11,[nt!KeServiceDescriptorTableShadow (fffff800`040b4880)]
fffff800`03e82780 f7830001000080000000 test dword ptr [rbx+100h],80hSSDT hook
https://blog.csdn.net/zfdyq0/article/details/26753797
源碼:
main.c
#include <hookssdt.h>
//驅動卸載函數
VOID DriverUnload(PDRIVER_OBJECT pDriver)
{
UnhookSSDT();
DbgPrint("Driver Unload\n");
}
//驅動入口函數
NTSTATUS DriverEntry(PDRIVER_OBJECT pDriver, PUNICODE_STRING pPath)
{
DbgPrint("Hello World\n");
//獲取KeServiceDescriptorTable
KeServiceDescriptorTable = (PSYSTEM_SERVICE_TABLE)GetKeServiceDescriptorTable64();
//開啓Hook
HookSSDT();
pDriver->DriverUnload = DriverUnload;
return STATUS_SUCCESS;
}hookssdt.h
#include <ntddk.h>
typedef struct _SYSTEM_SERVICE_TABLE {
PVOID ServiceTableBase;
PVOID ServiceCounterTableBase;
ULONGLONG NumberOfServices;
PVOID ParamTableBase;
} SYSTEM_SERVICE_TABLE, *PSYSTEM_SERVICE_TABLE;
typedef struct _SERVICE_DESCRIPTOR_TABLE {
SYSTEM_SERVICE_TABLE ntoskrnl; // ntoskrnl.exe (native api)
SYSTEM_SERVICE_TABLE win32k; // win32k.sys (gdi/user)
SYSTEM_SERVICE_TABLE Table3; // not used
SYSTEM_SERVICE_TABLE Table4; // not used
}SERVICE_DESCRIPTOR_TABLE, *PSERVICE_DESCRIPTOR_TABLE;
//NtTerminateProcess
typedef NTSTATUS(__fastcall *NTTERMINATEPROCESS)(IN HANDLE ProcessHandle, IN NTSTATUS ExitStatus);
NTKERNELAPI UCHAR * PsGetProcessImageFileName(PEPROCESS Process);
//SSDT表基址
PSYSTEM_SERVICE_TABLE KeServiceDescriptorTable;
NTTERMINATEPROCESS NtTerminateProcess = NULL;
ULONG OldTpVal;
//自己的NtTerminateProcess
NTSTATUS __fastcall Fuck_NtTerminateProcess(IN HANDLE ProcessHandle, IN NTSTATUS ExitStatus)
{
PEPROCESS Process;
NTSTATUS st = ObReferenceObjectByHandle(ProcessHandle, 0, *PsProcessType, KernelMode, &Process, NULL);
DbgPrint("Fake_NtTerminateProcess called!");
if (NT_SUCCESS(st))
{
if (!_stricmp(PsGetProcessImageFileName(Process), "calc.exe"))
return STATUS_ACCESS_DENIED;
else
return NtTerminateProcess(ProcessHandle, ExitStatus);
}
else
return STATUS_ACCESS_DENIED;
}
//關閉寫保護
KIRQL WPOFFx64()
{
KIRQL irql = KeRaiseIrqlToDpcLevel();
UINT64 cr0 = __readcr0();
cr0 &= 0xfffffffffffeffff;
__writecr0(cr0);
_disable();
return irql;
}
//開啓寫保護
void WPONx64(KIRQL irql)
{
UINT64 cr0 = __readcr0();
cr0 |= 0x10000;
_enable();
__writecr0(cr0);
KeLowerIrql(irql);
}
ULONGLONG GetKeServiceDescriptorTable64() //我的方法
{
PUCHAR StartSearchAddress = (PUCHAR)__readmsr(0xC0000082);
PUCHAR EndSearchAddress = StartSearchAddress + 0x500;
PUCHAR i = NULL;
UCHAR b1 = 0, b2 = 0, b3 = 0;
ULONG templong = 0;
ULONGLONG addr = 0;
for (i = StartSearchAddress;i < EndSearchAddress;i++)
{
if (MmIsAddressValid(i) && MmIsAddressValid(i + 1) && MmIsAddressValid(i + 2))
{
b1 = *i;
b2 = *(i + 1);
b3 = *(i + 2);
if (b1 == 0x4c && b2 == 0x8d && b3 == 0x15) //4c8d15
{
memcpy(&templong, i + 3, 4);
addr = (ULONGLONG)templong + (ULONGLONG)i + 7;
return addr;
}
}
}
return 0;
}
//獲取SSDT中的函數地址
ULONGLONG GetSSDTFuncCurAddr(ULONG id)
{
LONG dwtmp = 0;
PULONG ServiceTableBase = NULL;
ServiceTableBase = (PULONG)KeServiceDescriptorTable->ServiceTableBase;
dwtmp = ServiceTableBase[id];
dwtmp = dwtmp >> 4;
return (LONGLONG)dwtmp + (ULONGLONG)ServiceTableBase;
}
ULONG GetOffsetAddress(ULONGLONG FuncAddr)
{
ULONG dwtmp = 0;
PULONG ServiceTableBase = NULL;
ServiceTableBase = (PULONG)KeServiceDescriptorTable->ServiceTableBase;
dwtmp = (ULONG)(FuncAddr - (ULONGLONG)ServiceTableBase);
return dwtmp << 4;
}
//InlineHook_KeBugCheckEx
VOID FuckKeBugCheckEx()
{
KIRQL irql;
ULONGLONG myfun;
UCHAR jmp_code[] = "\x48\xB8\xFF\xFF\xFF\xFF\xFF\xFF\xFF\x00\xFF\xE0";
myfun = (ULONGLONG)Fuck_NtTerminateProcess;//替換成自己的函數地址
memcpy(jmp_code + 2, &myfun, 8);
irql = WPOFFx64();
memset(KeBugCheckEx, 0x90, 15);
memcpy(KeBugCheckEx, jmp_code, 12);
WPONx64(irql);
}
VOID HookSSDT()
{
KIRQL irql;
ULONGLONG dwtmp = 0;
PULONG ServiceTableBase = NULL;
//get old address
NtTerminateProcess = (NTTERMINATEPROCESS)GetSSDTFuncCurAddr(41);
DbgPrint("Old_NtTerminateProcess: %llx", (ULONGLONG)NtTerminateProcess);
//set kebugcheckex
FuckKeBugCheckEx();
//show new address
ServiceTableBase = (PULONG)KeServiceDescriptorTable->ServiceTableBase;
OldTpVal = ServiceTableBase[41]; //record old offset value
irql = WPOFFx64();
ServiceTableBase[41] = GetOffsetAddress((ULONGLONG)KeBugCheckEx);
WPONx64(irql);
DbgPrint("KeBugCheckEx: %llx", (ULONGLONG)KeBugCheckEx);
DbgPrint("New_NtTerminateProcess: %llx", GetSSDTFuncCurAddr(41));
}
VOID UnhookSSDT()
{
KIRQL irql;
PULONG ServiceTableBase = NULL;
ServiceTableBase = (PULONG)KeServiceDescriptorTable->ServiceTableBase;
//set value
irql = WPOFFx64();
ServiceTableBase[41] = GetOffsetAddress((ULONGLONG)NtTerminateProcess); //OldTpVal; //直接填寫這個舊值也行
WPONx64(irql);
//沒必要恢復KeBugCheckEx的內容了,反正執行到KeBugCheckEx時已經完蛋了。
DbgPrint("NtTerminateProcess: %llx", GetSSDTFuncCurAddr(41));
}