企業中ipsec的應用---------------Ipsec搭建×××案例
上篇ipsec協議解析---------傳送門
華爲設備
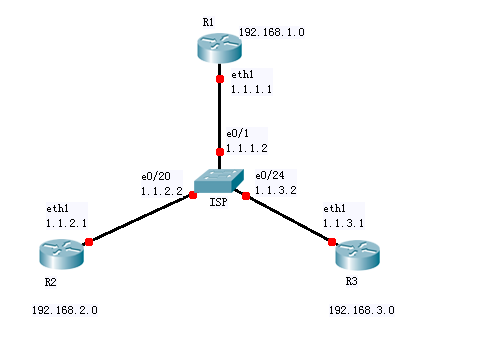
拓撲圖:
三層交換機充當ISP的internet配置結果:
通道一:R1----------------------R2
R1配置結果:
[R1]dis cu
Nowcreate configuration...
Current configuration
!
version 1.74
sysname R1
undo pos-server addr-switch
firewall enable
aaa-enable
aaa accounting-scheme optional
!
acl3000 match-order auto
rule normal permit ip source 192.168.1.0 0.0.0.255 destination192.168.2.0 0.0.0.255
!
ipsec proposal tran1
!
ipsec policy policy1 10 manual
security acl 3000
proposal tran1
tunnel local 1.1.1.1
tunnel remote 1.1.2.1
sa inbound esp spi 54321
sa inbound esp string-key qazwsx
sa outbound esp spi 12345
sa outbound esp string-key abcdefg
!
controller e1 0
!
interfaceAux0
async mode flow
link-protocol ppp
!
interface Ethernet0
loopback
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet1
ip address 1.1.1.1 255.255.255.0
ipsec policy policy1
!
interface Serial0
link-protocol ppp
!
interface Serial1
link-protocol ppp
!
quit
iproute-static 0.0.0.0 0.0.0.0 1.1.1.2 preference 60
!
Return
[R1]dis ipsec proposal
proposal set name: tran1
proposal set mode: tunnel
transform: esp-new
ESP protocol:authentication md5-hmac-96, encryption-algorithm des
[R1]dis ipsec policy all
ipsec policy name: policy1
ipsec policy sequence: 10
negotiation mode: manual
security acl: 3000
local address: 1.1.1.1
remote address: 1.1.2.1
proposal name: tran1
ah(inbound) setting:
ah spi:
ah string-key:
ah hex-key-string:
esp(inbound) setting:
esp spi: 54321 (0xd431)
esp string-key: qazwsx
esp encryption-hex:
esp authen-hex:
ah(outbound) setting:
ah spi:
ah string-key:
ah hex-key-string:
esp(outbound) setting:
esp spi: 12345 (0x3039)
esp string-key: abcdefg
esp encryption-hex:
esp authen-hex:
OutBound SA has been established.
InBound SA has been established.
R2配置結果:
[R2]dis cu
Nowcreate configuration...
Current configuration
!
version 1.74
sysname R2
firewall enable
aaa-enable
aaa accounting-scheme optional
!
acl3000 match-order auto
rule normal permit ip source 192.168.2.0 0.0.0.255 destination192.168.1.0 0.0.0.255
rule normal deny 20 source any destination any
!
ipsec proposal tran1
!
ipsec policy policy1 10 manual
security acl 3000
proposal tran1
tunnel local 1.1.2.1
tunnel remote 1.1.1.1
sa inbound esp spi 12345
sa inbound esp string-key abcdefg
sa outbound esp spi 54321
sa outbound esp string-key qazwsx
!
interface Aux0
async mode flow
link-protocol ppp
!
interface Ethernet0
loopback
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet1
ip address 1.1.2.1 255.255.255.0
ipsec policy policy1
!
interfaceSerial0
link-protocol ppp
!
interface Serial1
link-protocol ppp
!
quit
iproute-static 0.0.0.0 0.0.0.0 1.1.2.2 preference 60
!
Return
[R2]dis ipsec proposal
proposal set name: tran1
proposal set mode: tunnel
transform: esp-new
ESP protocol:authentication md5-hmac-96, encryption-algorithm des
[R2]dis ipsecpolicy all
ipsec policy name: policy1
ipsec policy sequence: 10
negotiation mode: manual
security acl: 3000
local address: 1.1.2.1
remote address: 1.1.1.1
proposal name: tran1
ah(inbound) setting:
ah spi:
ah string-key:
ah hex-key-string:
esp(inbound) setting:
esp spi: 12345 (0x3039)
esp string-key: abcdefg
esp encryption-hex:
esp authen-hex:
ah(outbound) setting:
ah spi:
ah string-key:
ah hex-key-string:
esp(outbound) setting:
esp spi: 54321 (0xd431)
esp string-key: qazwsx
esp encryption-hex:
esp authen-hex:
OutBound SA has been established.
InBound SA has been established.
通道二:R1------------------------------R3
在R1和R3的配置方法如同R1和R2的配置方法
結果測試:
R1 ping R2結果:
[R1]ping -a192.168.1.1 192.168.2.1
PING 192.168.2.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.2.1: bytes=56 Sequence=0ttl=255 time = 7 ms
Reply from 192.168.2.1: bytes=56 Sequence=1ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=2ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=3ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=4ttl=255 time = 3 ms
--- 192.168.2.1 ping statistics ---
5 packets transmitted
5packets received
0.00% packet loss
round-trip min/avg/max = 3/3/7 ms
R2 ping R1結果:
[R2]ping -a192.168.2.1 192.168.1.1
PING 192.168.1.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.1.1: bytes=56 Sequence=0ttl=255 time = 4 ms
Reply from 192.168.1.1: bytes=56 Sequence=1ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=2ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=3ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=4ttl=255 time = 3 ms
--- 192.168.1.1 ping statistics ---
5 packets transmitted
5 packets received
0.00% packet loss
round-trip min/avg/max = 3/3/4 ms
二、自動模式(適合節點多的大型網絡)
三層交換機的配置不用更改,只需對三臺路由器做修改。
通道一:R1----------------R2
R1路由器配置結果:
[R1]dis ipsec policy all
ipsec policy name: policy1
ipsec policy sequence: 10
negotiation mode: isakmp
security acl: 3000
remote address 0: 1.1.2.1
Proposal name: tran1
ipsec sa duration: 3600 seconds
ipsec sa duration: 1843200 kilobytes
OutBound SA has been established.
InBound SA has been established.
[R1]dis cu
Nowcreate configuration...
Current configuration
!
version 1.74
sysname R1
undo pos-server addr-switch
firewall enable
aaa-enable
aaa accounting-scheme optional
!
ikepre-shared-key 123 remote 1.1.2.1
!
acl3000 match-order auto
rule normal permit ip source 192.168.1.0 0.0.0.255 destination192.168.2.0 0.0.0.255
!
ipsec proposal tran1
!
ipsec policy policy1 10 isakmp
security acl 3000
proposal tran1
tunnel remote 1.1.2.1
!
controller e1 0
!
interface Aux0
async mode flow
link-protocol ppp
!
interface Ethernet0
loopback
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet1
ip address 1.1.1.1 255.255.255.0
ipsec policy policy1
!
interface Serial0
link-protocol ppp
!
interface Serial1
link-protocol ppp
!
quit
iproute-static 0.0.0.0 0.0.0.0 1.1.1.2 preference 60
!
Return
[R1] dis ipsec proposal
proposal set name: tran1
proposal set mode: tunnel
transform: esp-new
ESP protocol:authentication md5-hmac-96, encryption-algorithm des
[R1] dis ipsecpolicy all
ipsec policy name: policy1
ipsec policy sequence: 10
negotiation mode: isakmp
security acl: 3000
remote address 0: 1.1.2.1
Proposal name: tran1
ipsec sa duration: 3600 seconds
ipsec sa duration: 1843200 kilobytes
OutBound SA has been established.
InBound SA has been established.
R2路由器配置結果:
[R2]dis cu
Now create configuration...
Current configuration
!
version 1.74
sysname R2
firewall enable
aaa-enable
aaa accounting-scheme optional
!
ike pre-shared-key 123 remote 1.1.1.1
!
acl 3000 match-order auto
rule normal permit ip source 192.168.2.00.0.0.255 destination 192.168.1.0 0.0.0.255
rule normal deny 20 source any destinationany
!
ipsec proposal tran1
!
ipsec policy policy1 10 isakmp
security acl 3000
proposal tran1
tunnel remote 1.1.1.1
!
interface Aux0
async mode flow
link-protocol ppp
!
interface Ethernet0
loopback
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet1
ip address 1.1.2.1 255.255.255.0
ipsec policy policy1
!
interface Serial0
link-protocol ppp
!
interface Serial1
link-protocol ppp
!
quit
ip route-static 0.0.0.0 0.0.0.0 1.1.2.2preference 60
!
Return
[R2]dis ipsecproposal
proposal set name: tran1
proposal set mode: tunnel
transform: esp-new
ESP protocol: authentication md5-hmac-96,encryption-algorithm des
[R2]dis ipsecpolicy all
ipsec policy name: policy1
ipsec policy sequence: 10
negotiation mode: isakmp
security acl: 3000
remote address 0: 1.1.1.1
Proposal name: tran1
ipsec sa duration: 3600 seconds
ipsec sa duration: 1843200 kilobytes
OutBound SA has been established.
InBound SA has been established.
實驗結果測試:
R1 ping R2:
[R1]ping -a192.168.1.1 192.168.2.1
PING 192.168.2.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.2.1: bytes=56 Sequence=0ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=1ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=2ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=3ttl=255 time = 3 ms
Reply from 192.168.2.1: bytes=56 Sequence=4ttl=255 time = 3 ms
--- 192.168.2.1 ping statistics ---
5 packets transmitted
5 packets received
0.00% packet loss
round-trip min/avg/max = 3/3/3 ms
R2 ping R1:
[R2]ping -a192.168.2.1 192.168.1.1
PING 192.168.1.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.1.1: bytes=56 Sequence=0ttl=255 time = 7 ms
Reply from 192.168.1.1: bytes=56 Sequence=1ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=2ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=3ttl=255 time = 3 ms
Reply from 192.168.1.1: bytes=56 Sequence=4ttl=255 time = 3 ms
--- 192.168.1.1 ping statistics ---
5 packets transmitted
5packets received
0.00% packet loss
round-trip min/avg/max = 3/3/7 ms
通道二:R1----------------------R3
路由器R1與R3的配置過程如同R1與R2的通道配置。