現在我們個需求:允許內網主機訪問外部網絡,而外部網絡不能訪問我們的內網,如果我們使用router(config)#access-list {access-list-number} deny ip any any 並在指定接口調用,那麼,外部網絡是不能夠訪問內部網絡的,但內部網絡的數據出去之後也回不來了,顯然,我們並不想要這種結果。
我們知道TCP在建立連接之前,有一個三次握手過程,在TCP的包頭裏面有一個標誌位,我們的擴展訪問控制列表可以對這個標誌位進行控制。我們分析下,內部主機向外發起連接的時候,SYN位爲1,而外部的主機迴應包裏面爲 SYN=1 ACK=1,而一個外部主機要想內部發起連接,他的第一個包只是SYN=1,而ACK=0,所以,我們可以使用Established ACL來達到我們想要的結果,命令如
R2(config)#ip access-list extended tcp
R2(config-ext-nacl)#permit tcp any any established
並在指定接口調用,然而Established ACL有一個致命的缺陷,它必須指定某一應用,如TCP,但我們可能會用到UDP、ICMP、PING等,爲了解決這一問題,我們可以用自反ACL。接下來我們用實驗來一一說明。
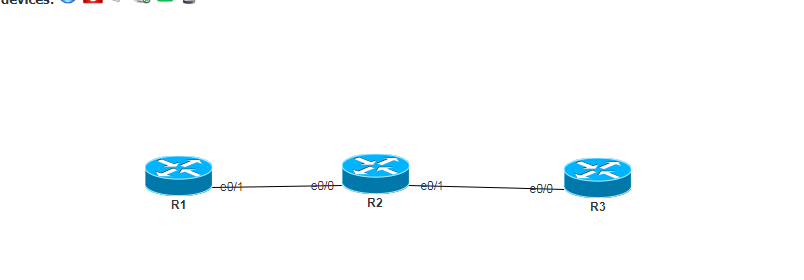
拓撲圖:
#**#要求:R1能夠Telnet到R3上,但R3不能夠Telnet到R1上。
一、配置路由,使網絡能夠互通
R1的配置
R1(config)#int lo 0
R1(config-if)#ip address 10.1.1.1 255.255.255.0
R1(config-if)#int e0/1
R1(config-if)#ip address 12.1.1.1 255.255.255.0
R1(config-if)#no shutdown
R1(config)#router ospf 100
R1(config-router)#router-id 10.1.1.1
R1(config-router)#network 10.1.1.1 0.0.0.0 a 0
R1(config-router)#network 12.1.1.1 0.0.0.0 a 0
R2的配置
R2(config)#int lo 0
R2(config-if)#ip address 10.2.2.2 255.255.255.0
R2(config-if)#int e0/0
R2(config-if)#ip address 12.1.1.2 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#int e0/1
R2(config-if)#ip address 23.1.1.2 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#exi
R2(config)#router ospf 100
R2(config-router)#router-id 10.2.2.2
R2(config-router)#network 10.2.2.2 0.0.0.0 a 0
R2(config-router)#network 12.1.1.2 0.0.0.0 a 0
R2(config-router)#network 23.1.1.2 0.0.0.0 a 0
R3的配置
R3(config)#int lo 0
R3(config-if)#ip address 10.3.3.3 255.255.255.0
R3(config-if)#int e0/0
R3(config-if)#ip address 23.1.1.3 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#exi
R3(config)#router ospf 100
R3(config-router)#router-id 10.3.3.3
R3(config-router)#network 10.3.3.3 0.0.0.0 a 0
R3(config-router)#network 23.1.1.3 0.0.0.0 a 0
測試
R1#ping 10.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.3.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/6 ms
R3#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/5 ms
二、配置Telnet
R1上配置Telnet
R1(config)#username xiaoming privilege 15 password xiaoming
R1(config)#line vty 0 4
R1(config-line)#login local
R1(config-line)#end
R3上配置Telnet
R3(config)#username xiaozhang privilege 15 password xiaozhang
R3(config)#line vty 0 4
R3(config-line)#login local
R3(config-line)#end
測試
R1#telnet 10.3.3.3
Trying 10.3.3.3 ... Open
User Access Verification
Username: xiaozhang
Password:
R3#
R1能夠Telnet到R3上
R1#ping 10.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.3.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/6 ms
R1能ping通R3
R3#telnet 10.1.1.1
Trying 10.1.1.1 ... Open
User Access Verification
Username: xiaoming
Password:
R1#
R3能夠Telnet到R1
R3#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
R3能ping通R1
由於並未做任何控制,R1與R3是可以相互Telnet的。
三、配置Established acl
R2(config)#ip access-list extended tcp //ACL的命名寫法
R2(config-ext-nacl)#permit tcp any any established
R2(config-ext-nacl)#permit ospf any any //保持ospf路由正常運行
R2(config)#int e0/1 //在in方向調用
R2(config-if)#ip access-group tcp in
測試
R1#telnet 10.3.3.3
Trying 10.3.3.3 ... Open
User Access Verification
Username: xiaozhang
Password:
R3#
R1能夠Telnet到R3
R1#ping 10.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.3.3.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R1不能ping通R3
這個時候,我們發現R1不能ping通R3了,原爲什麼呢?
我們在訪問控制列表中沒有允許ICMP協議,所以返回的數據包在R2上面被拒絕掉了,但是telnet成功了,因爲我們在進來的訪問控制列表裏允許了TCP。
R3#telnet 10.1.1.1
Trying 10.1.1.1 ...
% Destination unreachable; gateway or host down
R3#
R3不能夠Telnet到R1
R3#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R3不能ping通R1
我們看R3是不能訪問R1的任何東西了,爲什麼呢?ping不通的原因是我們在R2上阻止了ICMP,而telnet爲什麼不行呢,雖然我們允許了TCP包,但是因爲是R3向R1發起初始化連接,TCP裏面的標誌位SYN=1,ACK=0,而我們的訪問控制列表的關鍵詞established定義了只有ACK=1的包才能被允許,所以,這個初始連接包就被拒絕了,那麼我們這種做法就滿足了試驗要求。
但如果我們不僅想讓R1能Telnet到R3,還能夠ping通R3,可以用自反ACL
四、配置自反ACL
先在R2上刪除Established acl
然後再配置自反acl
R2(config)#ip access-list extended k1
R2(config-ext-nacl)#permit ip any any reflect zifanlist
R2(config-ext-nacl)#permit ospf any any
R2(config-ext-nacl)#exit
R2(config)#ip access-list extended k2
R2(config-ext-nacl)#evaluate zifanlist
R2(config-ext-nacl)#permit ospf any any
R2(config-ext-nacl)#exit
R2(config)#int e0/1
R2(config-if)#ip access-group k1 out
R2(config-if)#ip access-group k2 in
查看路由
R1#sho ip route
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Loopback0
L 10.1.1.1/32 is directly connected, Loopback0
O 10.2.2.2/32 [110/11] via 12.1.1.2, 01:29:18, Ethernet0/1
O 10.3.3.3/32 [110/21] via 12.1.1.2, 00:58:43, Ethernet0/1
12.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 12.1.1.0/24 is directly connected, Ethernet0/1
L 12.1.1.1/32 is directly connected, Ethernet0/1
23.0.0.0/24 is subnetted, 1 subnets
O 23.1.1.0 [110/20] via 12.1.1.2, 00:58:43, Ethernet0/1
R3#sho ip rou
R3#sho ip route
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
O 10.1.1.1/32 [110/21] via 23.1.1.2, 00:58:48, Ethernet0/0
O 10.2.2.2/32 [110/11] via 23.1.1.2, 00:58:48, Ethernet0/0
C 10.3.3.0/24 is directly connected, Loopback0
L 10.3.3.3/32 is directly connected, Loopback0
12.0.0.0/24 is subnetted, 1 subnets
O 12.1.1.0 [110/20] via 23.1.1.2, 00:58:48, Ethernet0/0
23.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 23.1.1.0/24 is directly connected, Ethernet0/0
L 23.1.1.3/32 is directly connected, Ethernet0/0
測試
R1#telnet 10.3.3.3
Trying 10.3.3.3 ... Open
User Access Verification
Username: xiaozhang
Password:
R3#
R1能夠Telnet到R3
R1#ping 10.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.3.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
R1能夠ping通R3
R3#telnet 10.1.1.1
Trying 10.1.1.1 ...
% Destination unreachable; gateway or host down
R3不能夠Telnet到R1
R3#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
R3也不能ping通R1
以上測驗可以看出,R1內網主機不僅能夠Telnet到R3內網主機,還能夠ping通R3內網主機,但R3卻不能夠訪問R1的任何數據。
寫的不好,以後會來補充。