ASA 5520(IOS version 8.4) IKEv2 IPSEC ***實驗配置
1.實驗TOP圖如下:
2.實驗目的:
使用IKEv2實現點到點的IPSEC***通信,即本示例中192.168.1.100和172.16.1.100之間實現***通信。
3.具體配置如下:
ASA1配置
interfaceGigabitEthernet0
nameif outside
security-level 0
ip address 11.1.1.2 255.255.255.0
!
interfaceGigabitEthernet1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
//以下是定義object,方便後面調用
objectnetwork Inside_network
subnet 192.168.1.0 255.255.255.0
objectnetwork ***_address //定義***遠端點的具體ip地址,即要實現點到點***的點ip
host 172.16.1.100
objectnetwork Inside_address //定義***本端點的具體ip地址,即要實現點到點***的點ip
host 192.168.1.100
access-list110 extended permit ip any any
access-list*** extended permit ip object Inside_address object ***_address //定義***興趣流
nat(inside,outside) source static Inside_address Inside_address destination static***_address ***_address //將***數據流和NAT分離
!
objectnetwork Inside_network
nat (inside,outside) dynamic interface //設置PAT
access-group110 in interface outside
routeoutside 0.0.0.0 0.0.0.0 11.1.1.1 1
cryptoipsec ikev2 ipsec-proposal TRAN //定義ipsec轉換集
protocol esp encryption aes-256
protocol esp integrity md5
cryptomap TEST 10 match address *** //定義crypto map,此處的“***”便是剛纔創建的***興趣流的ACL的名稱
cryptomap TEST 10 set peer 12.1.1.2 //設置***對端出口ip
cryptomap TEST 10 set ikev2 ipsec-proposal TRAN //調用剛纔創建的ipsec轉換集
cryptomap TEST interface outside //將其運用到outside端口
cryptoikev2 policy 10 //定義ikev2策略
encryption aes-256
integrity sha256 md5
group 2
prf sha256 md5
lifetime seconds 86400
cryptoikev2 enable outside //在outside端口啓用ikev2,這個很重要,如果不啓用,其餘都是浮雲
tunnel-group12.1.1.2 type ipsec-l2l //定義***隧道,類型爲ipsec-l2l
tunnel-group12.1.1.2 ipsec-attributes //定義***隧道屬性
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
ASA2配置:
interfaceGigabitEthernet0
nameif outside
security-level 0
ip address 12.1.1.2 255.255.255.0
!
interfaceGigabitEthernet1
nameif inside
security-level 100
ip address 172.16.1.1 255.255.255.0
objectnetwork Inside_network
subnet 172.16.1.0 255.255.255.0
objectnetwork Inside_address
host 172.16.1.100
objectnetwork ***_address
host 192.168.1.100
access-list110 extended permit ip any any
access-list*** extended permit ip object Inside_address object ***_address
nat(inside,outside) source static Inside_address Inside_address destination static***_address ***_address
!
objectnetwork Inside_network
nat (inside,outside) dynamic interface
access-group110 in interface outside
routeoutside 0.0.0.0 0.0.0.0 12.1.1.1 1
cryptoipsec ikev2 ipsec-proposal TRAN
protocol esp encryption aes-256
protocol esp integrity md5
cryptomap TEST 10 match address ***
cryptomap TEST 10 set peer 11.1.1.2
cryptomap TEST 10 set ikev2 ipsec-proposal TRAN
cryptomap TEST interface outside
cryptoikev2 policy 10
encryption aes-256
integrity sha256 md5
group 2
prf sha256 md5
lifetime seconds 86400
cryptoikev2 enable outside
tunnel-group11.1.1.2 type ipsec-l2l
tunnel-group11.1.1.2 ipsec-attributes
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
!
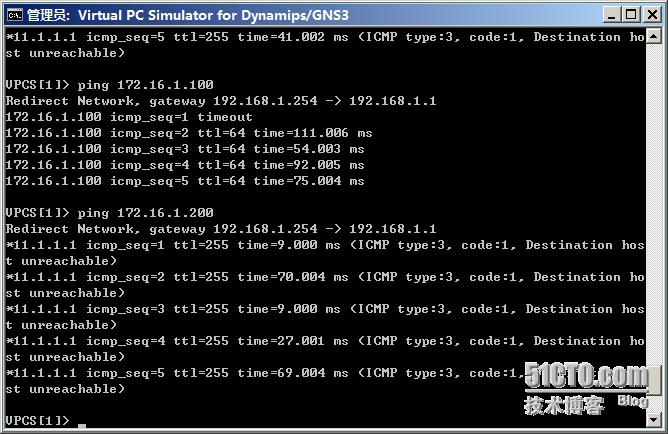
4.驗證:從192.168.1.100上ping的結果,和172.16.1.100可以通,和172.16.1.200不通。
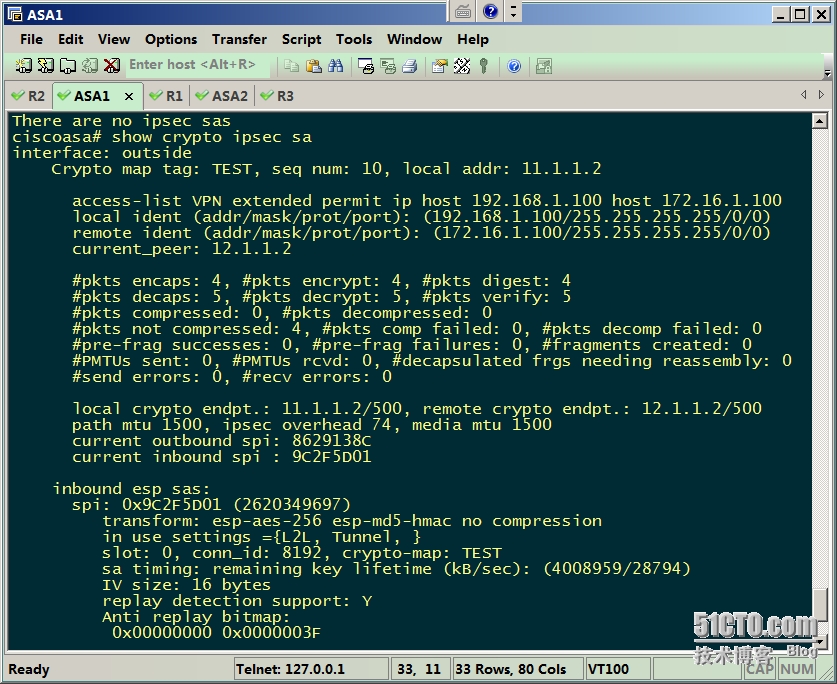
showcrypto ipsec sa的結果