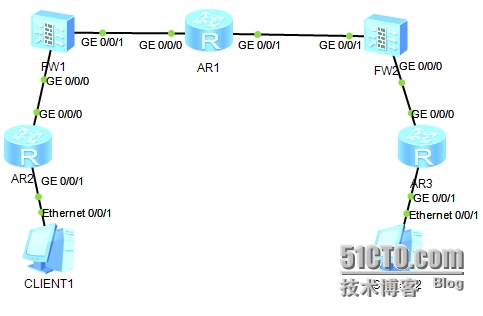
1.實驗拓撲:
使用模擬器eNSP(版本號:1.2.00.350 V100R002c00)+AR3260+USG5500
AR1模擬運營商
2.實驗需求:
a) 在FW1上做PAT,讓C1可以上互聯網
b) 在FW1和FW2之間做IPsec***,讓C1、C2間實現私網通信
3.實驗步驟:
a) IP地址規劃:
FW1 | GE0/0/0 |
| AR1 | GE0/0/0 |
|
GE0/0/1 |
| GE0/0/1 |
| ||
FW2 | GE0/0/0 |
| AR2 | GE0/0/0 |
|
GE0/0/1 |
| GE0/0/1 |
| ||
AR3 | GE0/0/0 |
| C1 |
| |
GE0/0/1 |
| C2 |
|
b) 配置腳本如下:
FW1
<SRG>sy //進入系統視圖
[SRG]sysnameFW1 //修改設備名稱
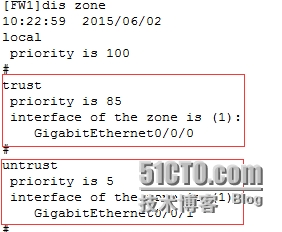
[FW1]firewallzone trust //進入trust區域
[FW1-zone-trust]addint g0/0/0 //把g0/0/0接口加入到trust區域中
[FW1-zone-trust]q //退出到上一層模式
[FW1]firewallzone untrust
[FW1-zone-untrust]addint g0/0/1
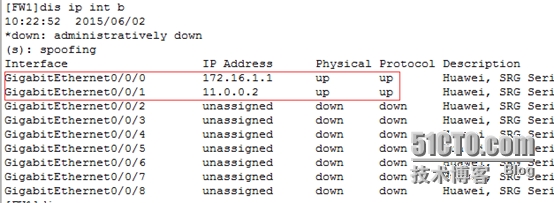
[FW1-zone-untrust]intg0/0/0 //進入接口視圖
[FW1-GigabitEthernet0/0/0]ipadd 172.16.1.1 24 //配置IP地址
[FW1-GigabitEthernet0/0/0]intg0/0/1
[FW1-GigabitEthernet0/0/1]ipadd 11.0.0.2 24
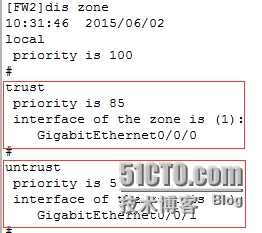
[FW1]dis zone //查看區域
[FW1]disip int b //查看接口IP地址
AR1
<Huawei>sy
[Huawei]sysnameAR1
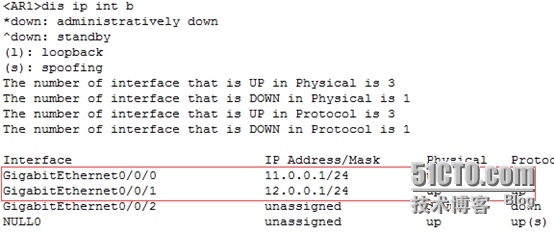
[AR1]intg0/0/0
[AR1-GigabitEthernet0/0/0]ipadd 11.0.0.1 24
[AR1-GigabitEthernet0/0/0]intg0/0/1
[AR1-GigabitEthernet0/0/1]ipadd 12.0.0.1 24
<AR1>disip int b
FW2
<SRG>sy
[SRG]sysnameFW2
[FW2]firewallzone trust
[FW2-zone-trust]addint g0/0/0
[FW2-zone-trust]q
[FW2]firewallzone untrust
[FW2-zone-untrust]addint g0/0/1
[FW2-zone-untrust]intg0/0/0
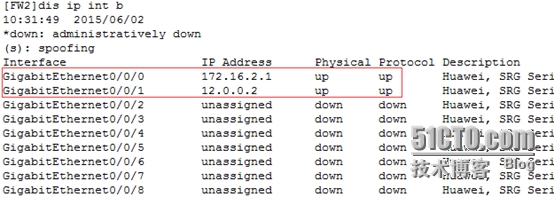
[FW2-GigabitEthernet0/0/0]ipadd 172.16.2.1 24
[FW2-GigabitEthernet0/0/0]intg0/0/1
[FW2-GigabitEthernet0/0/1]ipadd 12.0.0.2 24
[FW2]diszone
[FW2]disip int b
AR2
<Huawei>sy
[Huawei]sysnameAR2
[AR2]intg0/0/0
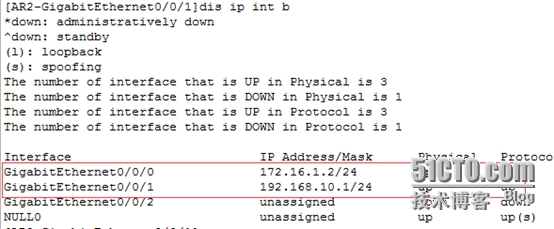
[AR2-GigabitEthernet0/0/0]ipadd 172.16.1.2 24
[AR2-GigabitEthernet0/0/0]intg0/0/1
[AR2-GigabitEthernet0/0/1]ip add 192.168.10.1 24
[AR2-GigabitEthernet0/0/1]disip int b
AR3
<Huawei>sy
[Huawei]sysnameAR3
[AR3]intg0/0/0
[AR3-GigabitEthernet0/0/0]ipadd 172.16.2.2 24
[AR3-GigabitEthernet0/0/0]intg0/0/1
[AR3-GigabitEthernet0/0/1]ipadd 192.168.20.1 24
[AR3-GigabitEthernet0/0/1]disip int b
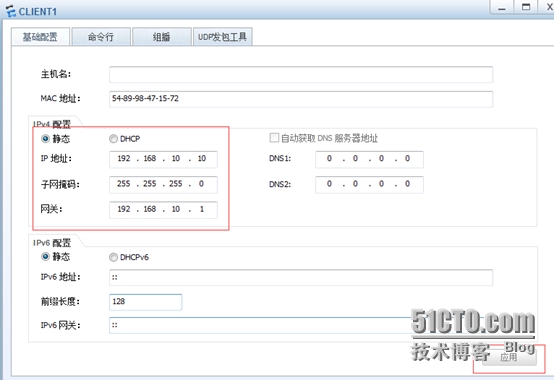
C1
C2
-----------------------以上是IP地址配置-------------------------
FW1
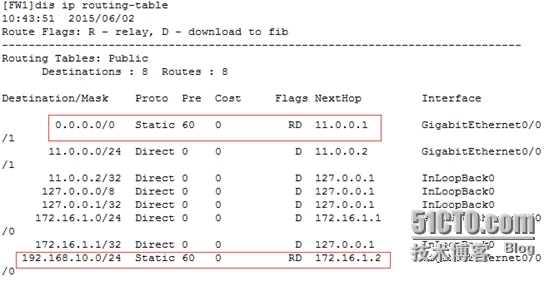
[FW1]iproute-static 0.0.0.0 0 11.0.0.1 //出口做默認路由
[FW1]iproute-static 192.168.10.0 24 172.16.1.2 //向下指靜態路由
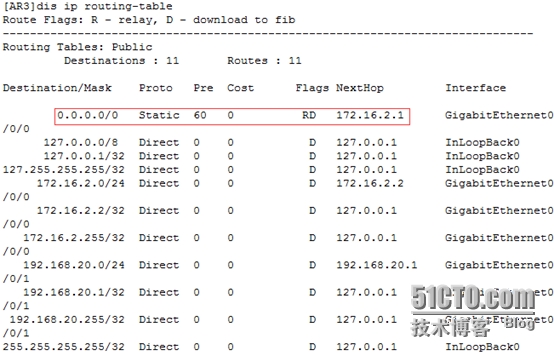
[FW1]disip routing-table //查看路由表
FW2
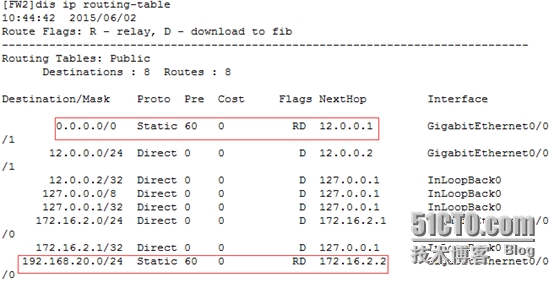
[FW2]iproute-static 0.0.0.0 0 12.0.0.1
[FW2]iproute-static 192.168.20.0 24 172.16.2.2
[FW2]disip routing-table
AR2
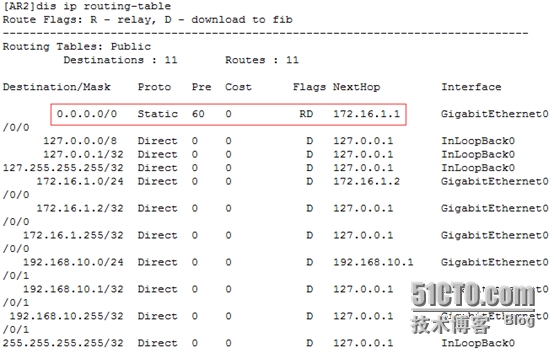
[AR2]iproute-static 0.0.0.0 0 172.16.1.1
[AR2]disip routing-table
AR3
[AR3]iproute-static 0.0.0.0 0 172.16.2.1
[AR3]disip routing-table
--------------------一上是路由配置--------------------------
FW1
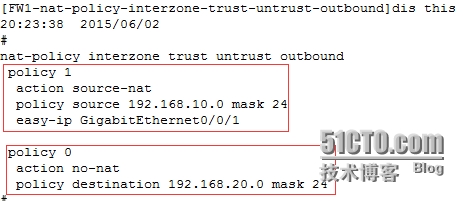
[FW1]nat-policyinterzone trust untrust outbound //進入域間NAT策略視圖
[FW1-nat-policy-interzone-trust-untrust-outbound-1]policy source 192.168.10.0mask 24 //創建NAT策略並進入策略視圖
[FW1-nat-policy-interzone-trust-untrust-outbound-1]actionsource-nat //指定需匹配流量的源地址
[FW1-nat-policy-interzone-trust-untrust-outbound-1]easy-ipg0/0/1 //直接使用接口IP作爲轉換地址
因爲防火牆默認拒絕ICMP流量通過,所以需要做以下配置
[FW1]policyinterzone trust untrust outbound //進入域間的outbound方向
[FW1-policy-interzone-trust-untrust-outbound]policy1 //創建轉發策略
[FW1-policy-interzone-trust-untrust-outbound-1]policy source 192.168.10.0mask 24 //當源是這個網段的時
[FW1-policy-interzone-trust-untrust-outbound-1]actionpermit //允許通過
測試C1上互聯網
---------------------以上是PAT配置---------------------
FW1
[FW1]acl3001
[FW1-acl-adv-3001]rule permit ip source 192.168.10.0 0.0.0.255 destination192.168.20.0 0.0.0.255 //配置感興趣流
[FW1-acl-adv-3001]ikeproposal 1 //創建IKE安全提議,並進入IKE安全提議視圖
[FW1-ike-proposal-1]encryption-algorithmaes-cbc //配置加密算法
[FW1-ike-proposal-1]authentication-methodpre-share //配置認證方法
[FW1-ike-proposal-1]authentication-algorithmsha1 //配置認證算法
[FW1-ike-proposal-1]dhgroup2 //配置DH組標識
[FW1-ike-proposal-1]ikepeer a //創建IKE Peer,並進入IKE Peer視圖
[FW1-ike-peer-a]ike-proposal1 //引用已配置的IKE安全提議
[FW1-ike-peer-a]pre-shared-keyabc123 //配置預共享密鑰認證,abc123是祕鑰
[FW1-ike-peer-a]remote-address12.0.0.2 //指定對端發起IKE協商的地址
[FW1-ike-peer-a]ipsecproposal tran1 //創建安全提議,並進入安全提議視圖
[FW1-ipsec-proposal-tran1]transformesp //配置傳送數據時採用的安全協議
[FW1-ipsec-proposal-tran1]espauthentication-algorithm sha1 //配置ESP方式採用的認證算法
[FW1-ipsec-proposal-tran1]espencryption-algorithm aes //配置ESP協議使用的加密算法
[FW1-ipsec-proposal-tran1]ipsecpolicy map1 10 isakmp //創建安全策略,並進入安全策略視圖
[FW1-ipsec-policy-isakmp-map1-10]securityacl 3001 //在安全策略中引用已創建的感興趣流
[FW1-ipsec-policy-isakmp-map1-10]proposaltran1 //在安全策略中引用已創建的安全提議
[FW1-ipsec-policy-isakmp-map1-10]ike-peera //在安全策略中引用IKE Peer
[FW1-ipsec-policy-isakmp-map1-10]intg0/0/1
[FW1-GigabitEthernet0/0/1]ipsecpolicy map1 //把安全策略應用到出口
FW2
[FW2]acl3001
[FW2-acl-adv-3001]rule permit ip source 192.168.20.0 0.0.0.255 destination192.168.10.0 0.0.0.255
[FW2-ike-proposal-1]encryption-algorithmaes-cbc
[FW2-ike-proposal-1]authentication-methodpre-share
[FW2-ike-proposal-1]authentication-algorithmsha1
[FW2-ike-proposal-1]dhgroup2
[FW2-ike-proposal-1]ikepeer a
[FW2-ike-peer-a]pre-shared-keyabc123
[FW2-ike-peer-a]remote-address11.0.0.2
[FW2-ike-peer-a]ipsecproposal tran1
[FW2-ipsec-proposal-tran1]transformesp
[FW2-ipsec-proposal-tran1]espauthentication-algorithm sha1
[FW2-ipsec-proposal-tran1]espencryption-algorithm aes
[FW2-ipsec-proposal-tran1]ipsecpolicy map1 10 isakmp
[FW2-ipsec-policy-isakmp-map1-10]securityacl 3001
[FW2-ipsec-policy-isakmp-map1-10]proposaltran1
[FW2-ipsec-policy-isakmp-map1-10]ike-peera
[FW2-ipsec-policy-isakmp-map1-10]intg0/0/1
[FW2-GigabitEthernet0/0/1]ipsecpolicy map1
--------------------以上是IPsec ***配置-------------------
FW1
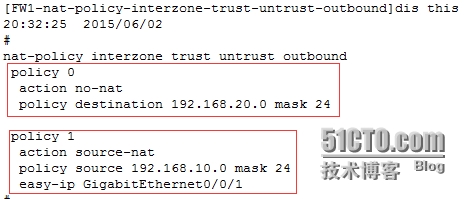
[FW1]nat-policyinterzone trust untrust outbound //進入域間的outbound方向
[FW1-nat-policy-interzone-trust-untrust-outbound]policy0 //創建轉發策略
[FW1-nat-policy-interzone-trust-untrust-outbound-0]policydestination 192.168.20.0 mask 24 //當目標是這個網段時
[FW1-nat-policy-interzone-trust-untrust-outbound-0]actionno-nat //不被NAT
因爲NAT策略優先級是從前往後依次執行的,所以需要把不被NAT的策略調到前面
[FW1-nat-policy-interzone-trust-untrust-outbound]policymove 0 before 1 //將policy 0優先級調整到policy 1的前面
-----------------以上是感興趣流出去時不被NAT---------------
FW1
因爲防火牆默認拒絕ICMP流量通過,所以需要做以下配置
[FW1]policyinterzone local untrust inbound //進入域間的inbound方向
[FW1-policy-interzone-local-untrust-inbound]policy 0 //創建轉發策略
[FW1-policy-interzone-local-untrust-inbound-0]policysource 12.0.0.2 0 //當源是這個主機時
[FW1-policy-interzone-local-untrust-inbound-0]actionpermit //允許通過
FW2
[FW2]policyinterzone local untrust inbound
[FW2-policy-interzone-local-untrust-inbound]policy1
[FW2-policy-interzone-local-untrust-inbound-1]policysource 11.0.0.2 0
[FW2-policy-interzone-local-untrust-inbound-1]actionpermit
測試建立IPsec***的兩端是否可以通信
因爲建立IPsec***需要兩端可以正常通信,所以需要做以上配置
-----------------以上是配置兩端防火牆可以正常通信---------------
FW2
[FW2]policyinterzone trust untrust outbound
[FW2-policy-interzone-trust-untrust-outbound]policy1
[FW2-policy-interzone-trust-untrust-outbound-1]policy source 192.168.20.0mask 24
[FW2-policy-interzone-trust-untrust-outbound-1]actionpermit
----------------以上是配置允許C2這邊流量可以出去-----------------
[FW1]policyinterzone trust untrust inbound //進入域間的inbound方向
[FW1-policy-interzone-trust-untrust-inbound]policy1
[FW1-policy-interzone-trust-untrust-inbound-1]policysource 192.168.20.0 mask 24
[FW1-policy-interzone-trust-untrust-inbound-1]policydestination 192.168.10.0 mask 24
[FW1-policy-interzone-trust-untrust-inbound-1]actionpermit
FW2
[FW2]policyinterzone trust untrust inbound
[FW2-policy-interzone-trust-untrust-inbound]policy1
[FW2-policy-interzone-trust-untrust-inbound-1]policysource 192.168.10.0 mask 24
[FW2-policy-interzone-trust-untrust-inbound-1]policydestination 192.168.20.0 mask 24
[FW2-policy-interzone-trust-untrust-inbound-1]actionpermit
------------------以上是配置允許流量可以進------------------
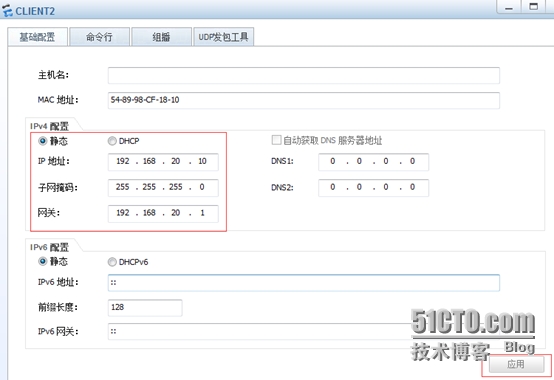
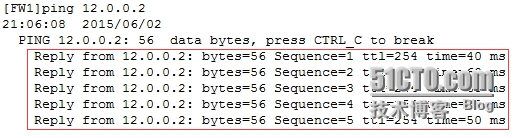
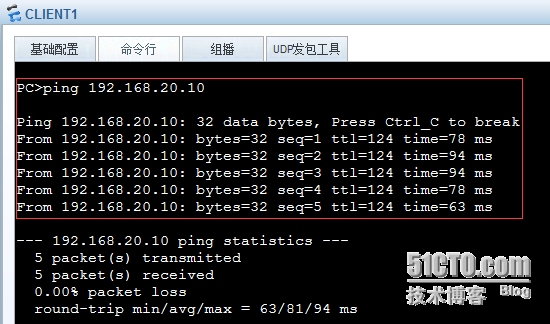
4.驗證結果:
驗證C1與C2之間私網通信



![TJ]AK4{L9@XQ_R(]SFXEQCQ.png wKiom1VtuDbSdaDrAAJSIA6aOZo258.jpg](http://s3.51cto.com/wyfs02/M02/6D/DF/wKiom1VtuDbSdaDrAAJSIA6aOZo258.jpg)