20161219 08:51——09:30
這篇博文記錄HoneyDrive_3_Royal_Jelly(1)系統應用整體的簡介和(2)初期準備或相關具體功能的介紹說明,和(3)HoneyDrive_3的基本使用或基礎理論。
參考:HoneyDrive (全局性介紹HoneyDrive的文章,不偏不倚)
https://bruteforce.gr/honeydrive
一、系統應用整體的簡介
參考: http://bruteforce.gr/honeydrive-3-royal-jelly-edition.html
HoneyDrive is the premier honeypot Linux distro. It is a virtual
appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed. It
contains over 10 pre-installed and pre-configured honeypot software
packages such as Kippo SSH honeypot, Dionaea and Amun malware honeypots,
Honeyd low-interaction honeypot, Glastopf web honeypot and Wordpot,
Conpot SCADA/ICS honeypot, Thug and PhoneyC honeyclients and more. Additionally it includes many useful pre-configured scripts and
utilities to analyze, visualize and process the data it can capture,
such as Kippo-Graph, Honeyd-Viz, DionaeaFR, an ELK stack and much more. Lastly, almost 90 well-known malware analysis, forensics and network
monitoring related tools are also present in the distribution.
20161219 11:10——12:39
What you need to know (PLEASE READ):
1) HoneyDrive 3 has been created entirely from scratch. It is based on Xubuntu Desktop 12.04.4 LTS edition and it is distributed as a standalone OVA file that can be easily imported as a virtual machine using virtualization software such as VirtualBox and VMware.
2) All the honeypot programs from the previous version of HoneyDrive are included, while they have also been upgraded to their latest versions and converted almost entirely to cloned git repos for easier maintenance and updating. This latter fact on its own could be considered reason enough to release the new version.
3) Many new honeypot programs have been installed that really make HoneyDrive 3 “complete” in terms of honeypot technology, plus around 50(!) new security related tools in the fields of malware analysis, forensics and network monitoring.
4) The main honeypot software packages and BruteForce Lab’s projects reside in /honeydrive. The rest of the programs reside in /opt. The location of all software can be found inside the README.txt file on the desktop.
5) HoneyDrive 3 doesn’t make itself as known to the outside world as the previous version. There are no descriptive messages and apart from Kippo-Graph and Honeyd-Viz every other piece of software is not accessible from the outside (unless if you configure them otherwise, or even lock down Kippo-Graph and Honeyd-Viz as well).
A note on versioning: previous versions of HoneyDrive started with a zero (0.1 and 0.2) which seemed confusing to some. I didn’t like it either and in the end I decided to “renumber” those as versions 1 and 2, essentially making this new version HoneyDrive 3, .i.e the third official release.
二、HoneyDrive使用前的初期準備或相關具體功能的介紹說明
參考:HoneyDrive 3 VMware guide
https://bruteforce.gr/honeydrive-3-vmware-guide.html
Here is a step by step guide for converting the HoneyDrive 3 OVA file to a VMware-compatible virtual machine. The procedure should be the same for all the other VMware products as well (Workstation, ESXi, etc). Instructions:
2.1 HoneyDrive_3在VMware中使用的前期準備工序:
(1).下載OVF Tool (:Download OVF Tool 3.5.2 (needs a free account registration)from: https://my.vmware.com/web/vmware/details?downloadGroup=OVFTOOL352&productId=352
(2). 安裝、運行OVF Tool,將OVA格式文件轉換爲VMX格式,(Convert HoneyDrive OVA to VMX)
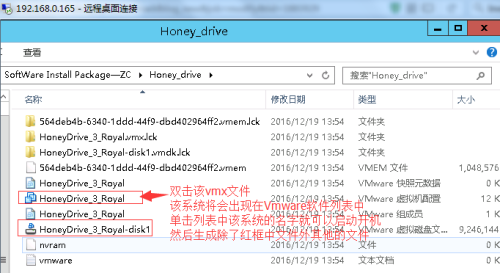
(3).將VMX格式文件(Honey)導入到vmware中,通過雙擊.vmx文件的方式(Import/open the new virtual machine by double clicking the .vmx file.)。
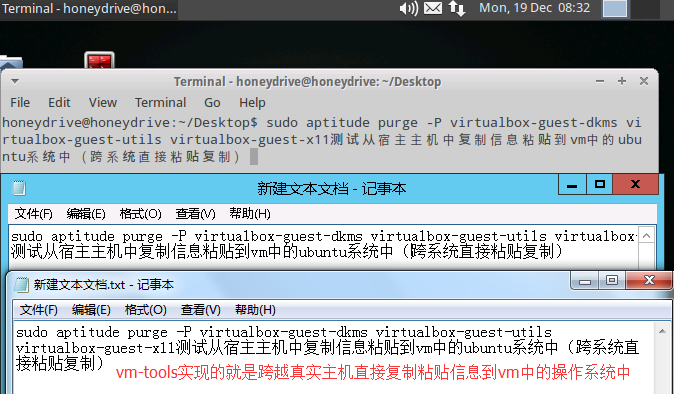
(4).在HoneyDrive virtual machine中的終端界面裏卸載VirtualBox Guest Additions(Inside the HoneyDrive virtual machine, open Terminator (on the desktop) and type the following to uninstall the VirtualBox Guest Additions):
$ sudo aptitude purge -P virtualbox-guest-dkms virtualbox-guest-utils virtualbox-guest-x11$ sudo reboot
備註:這裏卸載VirtualBox Guest Addition時需要提供用戶密碼,密碼信息可以在桌面上名爲“README”的文件中[System]裏找到。
(5).安裝VMware Tools(認爲這一步驟是可選的),Once HoneyDrive is running again, click on “Virtual
Machine” –> “Install VMware Tools” from the menu. This will mount a
virtual disk with VMware Tools. Open Terminator again and type:
$ cp /media/VMware\ Tools/VMwareTools-<version>.tar.gz ~/
$ tar zxvf VMwareTools-<version>.tar.gz
$ cd vmware-tools-distrib
$ sudo ./vmware-install.pl -d
$ sudo reboot
VMware Tools安裝完畢並重啓系統後,可以實現跨越真實主機zh直接傳遞數據到虛擬主機當中,即是實現直接從真實主機複製信息或文件到虛擬主機中(宿主主機或其他主機,比如下面是從宿主主機server2012直接粘貼信息到虛擬主機,還有從遠程登錄連接到宿主主機的主機win7中直接複製信息到虛擬主機中),見下圖:
That’s it, enjoy HoneyDrive in VMware!
2.2 工序中,關於在windows中OVF Tool的使用
關於詳盡的ovf的信息,參考:https://www.vmware.com/support/developer/ovf/
本次實踐中,是在windows的dos終端界面使用的ovf tool。用法如下:
(1)快捷鍵win+R打開“運行”交互界面輸入“cmd”進入dos界面
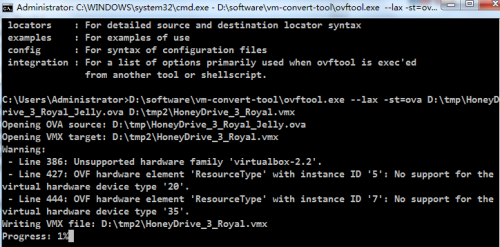
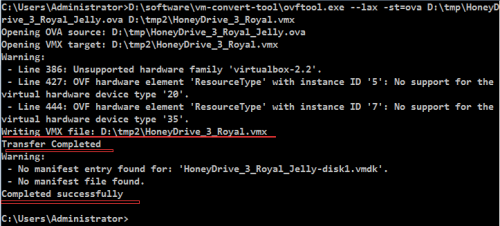
(2)命令行中輸入 D:\software\vm-convert-tool\ovftool.exe --lax -st=ova D:\tmp\HoneyDrive_3_Royal_Jelly.ova D:\tmp2\HoneyDrive_3_Royal_Jelly.vmx,直接回車,即進入格式轉換模式。如下圖:
備註:(0)之所以嘗試dos命令行,是因爲在圖形界面中安裝完畢ovftool之後既沒有啓動快捷圖標也沒有可用於有效啓動該工具的exe文件(1)關於命令中選項和參數的含義可以通過執行命令 D:\software\vm-convert-tool\ovftool.exe --help來了解。(2)命令中,D:\software\vm-convert-tool\ovftoolD:\tmp是存放HoneyDrive_3_Royal_Jelly.ova的路徑, D:\tmp2是新建的空的用於存放轉換vmx格式文件的路徑。(3)上述命令行之所以要使用絕對路徑,是因爲該應用沒有加入windows的全局環境配置,或說沒有加入成功,關於win7中全局環境變量的配置參考如下鏈接(本次實踐中沒有配置成功):
OVFTool 4.1 vmdk格式換成OVF格式
http://blog.csdn.net/hanzheng260561728/article/details/51345481
Adding the OVF Tool to your Path Environment Variable
The following instructions are for Windows 7, but the steps are similar on other Windows systems :
Right-click My Computer.
Select Properties.
Select Advanced system settings.
Select Environment Variables.
Highlight (select) the Path variable from the System variable (lower) pane.
Click the Edit button and then type the path to the folder where you installed the OVF Tool (at the end of the existing path).
2.3 工序中,將VMX格式文件導入到vmware中的操作
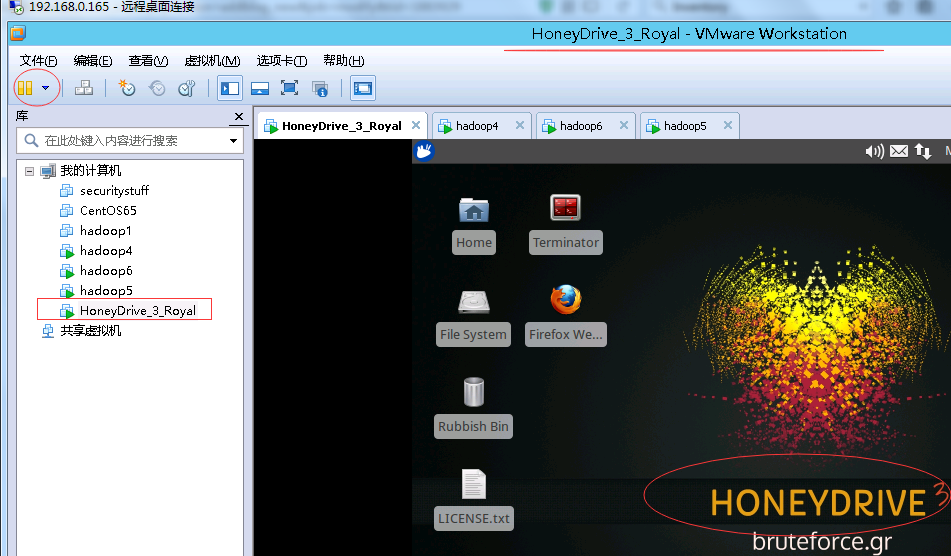
通過雙擊HoneyDrive_3_Royal的“.vmx”文件的方式,將HoneyDrive的系統名HoneyDrive_3_Royal導入到vmware的虛擬機列表中,然後在vmware的虛擬機列表中選中該系統名稱,單機菜單欄下方的“開啓此客戶機操作系統”綠色按鈕就可以開啓該操作系統。即是說,HoneyDrive_3應用套件是預安裝在ubuntu操作系統中的,HoneyDrive_3_Royal_Jelly.ova文件是現成的組裝好後生成的虛擬機文件(而不是需要先安裝ubuntu系統而後手工將套件安裝放置到ubuntu中),直接可以使用,只是爲了在Vmware中使用所以要將其格式轉換爲vmx。
20161219 16:17——17:51
三、HoneyDrive_3的基本使用或基礎理論
參考:Getting started with honeyd
https://bruteforce.gr/getting-started-honeyd.html
3.1 ubuntu操作系統的基礎配置和常用管理命令
參考:Ubuntu12.04 系統初始化
blog.csdn.net/yangfanabc1993/article/details/23677285
安裝過ubuntu 12.04 後需要做的幾件事
http://blog.163.com/likaifeng@126/blog/static/320973102012620550682/
(0.1)更新源數據,更新所有的軟件和安全補丁 。
sudo apt-get update 或者使用更新管理器更新軟件。
(0.2)安裝ssh服務端,sudo apt-get install openssh-server
(1)查看ssh服務端進程,ps -ef|grep sshd; sudo service ssh status
(2)開啓、終止sshd進程,sudo service ssh start
20161219 20:16——22:56
(3)網卡配置文件、主機名的配置、本地主機名&IP(域名解析)的hosts綁定配置
參考:Ubuntu通過修改配置文件進行網絡配置
http://blog.chinaunix.net/uid-22117508-id-157758.html
配置網卡,sudo vim /etc/network/interfaces,內容如下:
#======defualt settings====================
#auto lo #本部分是網卡文件中的自有的默認配置信息
#iface lo inet loopback
#======dhcp pattern========================
#auto eth0 #本部分是手工添加,自動獲取IP模式的eth0
#iface eth0 inet dhcp
#======static ip =========================
auto eth0 #本部分是手工添加,靜態IP模式的eth0,未註釋,生效
iface eth0 inet static
address 192.168.0.16
netmask 255.255.255.0
gateway 192.168.0.1
#pre-up ifconfig eth0 hw ether xx:xx:xx:xx:xx:xx(修改MAC)
重啓網卡eth0,ifdown eth0;ifup eth0
重啓網絡服務,sudo /etc/init.d/networking restart
添加域名解析服務器,sudo /etc/resolv.conf
主機名的配置,sudo vim /etc/hostname
本地域名解析綁定配置,sudo vim /etc/hosts
(4)防火牆進程的開啓與關閉以及配置
參考:
IptablesHowTo
https://help.ubuntu.com/community/IptablesHowTo
ubuntu下iptables的用法
http://blog.sina.com.cn/s/blog_537517170102vkpy.html
Ubuntu Server 12.04 配置防火牆iptables
http://blog.csdn.net/supercrsky/article/details/17553289
iptables:
ufw:sudo ufw enable;sudo ufw disable;sudo ufw status
官網描述:When you install Ubuntu, iptables is there, but it allows all traffic by default. Ubuntu 8.04 Comes with ufw - a program for managing the iptables firewall easily.——所以鑑於iptables配置策略的理論盤根錯節和並不影響當前實踐,故先將本部分理論基礎擱置,從長計議。
(5)修改對應於centos中yum源的“Download from”的源
這裏多見於圖形界面中處理。
(6)操作系統信息查看
查看操作系統的位數,getconf LONG_BIT
查看當前Ubuntu系統的版本,<1> cat /proc/version # proc目錄下記錄的當前系統運行的各種數據,version記錄的版本信息可以直接通過cat查看到,還可以看到gcc版本,但這裏不是普通的發行版本號。<2>uname -a #顯示自己的內核版本 <3>lsb_release -a #顯示版本描述和正規的發行版本號 <4> cat /etc/issue #只顯示發行版本號
查看CPU信息,cat /proc/cpuinfo
(7)ubuntu軟件包管理工具的使用
參考:Ubuntu Equivalent of Yum's WhatProvides
http://stackoverflow.com/questions/4471327/ubuntu-equivalent-of-yums-whatprovides
SwitchingToUbuntu/FromLinux/RedHatEnterpriseLinuxAndFedora
https://help.ubuntu.com/community/SwitchingToUbuntu/FromLinux/%20RedHatEnterpriseLinuxAndFedora
關於Ubuntu下apt的一些用法及和yum的比較
http://blog.sina.com.cn/s/blog_49b1f7210102vepr.html
<1>apt-file search ssh 與yum whatprovides */ssh
備註:yum反向查詢命令或文件所屬軟件包的命令其實已經由參數“whatprovides”改爲了“provides”,這點可以通過“yum --help”查證,但是前者還是可以使用的。相應地,ubuntu/debian系列的linux操作系統中使用的是apt-file來實現等效的反向查詢。
apt-file search ssh的使用:首先,如果apt-file不存在,使用apt-get install apt-file進行安裝;而後,新裝的apt-file需要先執行apt-file update;最後才能使用apt-file search|find ssh
注意:apt-file search XYZ的使用與等效的yum provides XYZ使用格式不同,前者不用使用“*/”