網絡工程師成長日記373-李寧公司項目
這是我的第373篇原創文章,記錄網絡工程師行業的點點滴滴,結交IT行業有緣之人
網絡設備割接工程項目技術回憶錄
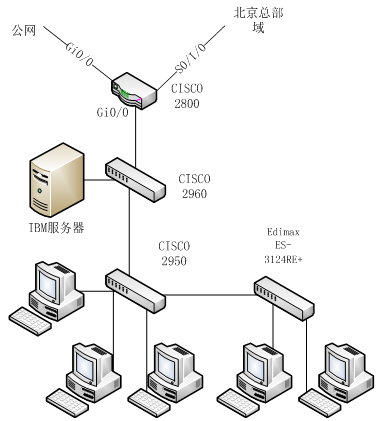
網絡環境拓撲圖如下:
圖1 上面的2臺爲IBM的服務器,白色爲協轉,再下來是28,再下面是交換機
圖2 接×××線的設備就是這次擔當替代品的2621
李寧西安分部現行的網絡環境是:一臺CISCO28系列路由器,2T的S口通過協轉接電信的光纖通往北京總部,其上承載着李寧公司整個域的一個管理
西安分部的人必須通過到北京域的驗證才能成功登陸到李寧的域,Gi0/0口接光纖直接連到外網, Gi0/1接口下配置n多子接口做單臂路由分別對應不同的部門
Gi0/1口下接一臺CISCO2960的F0/24口,2960的F0/24口配TRUNK,native vlan 10,其他接口下access mode都做DOT1X認證,配置有vlan 10 的svi地址,默認網關指的是28路由器
還配有radius-server,F0/23接口TRUNK下接另一臺CISCO2950,2950也配有vlan 10的svi地址,默認網關指向路由器,配有radius-server,其他接口下做DOT1X認證,有個接口接了臺愛迪麥斯 Edimax ES-3124RE+的24×××換機用來拓展接口。
這裏只有IBM服務器和財務部是直接連接公網並不通過域的。
組圖3 EDIMAX,這次去長見識了,以前我從未聽過有此品牌
我要做的工作就是:
1把現在的28路由器的配置抓取下來,以供比對刷進用來替代的2621裏,並把2950、2960的配置抓下來,以供研究爲什麼換上26之後網絡不通
2把28的線拔下來接到2621上,測試非域內網絡狀況,結果暢通
3測試域內網絡狀況,結果不通,排查原因,讓域成員離開域再進域重新認證,最終暢通
4把2621上架,回收28路由器
5再次反覆測試整個網絡的暢通情況,一切正常
6清理現場爲我們進來之前的狀態
就這麼幾步,要說基本沒什麼難度,和傳說中的大相徑庭。
做完之後,我覺得如果真是這麼簡單的話,怎麼可能第5次去才搞定,所以仔細詢問王老師每一次的經過,出現的問題,以及是怎麼結束的,記憶中是這樣:第一次是因爲2T模塊插上認不到,第二次是IOS問題,第三次是換上26非域內網絡暢通,第四次是換上26域內域外網絡都不通,並且vlan間路由ping不通。Vlan間路由ping不通,這個就是真正問題的疑點,我繼續詢問王老師,王老師說和北京那邊的網管溝通後,北京的網管說配置是沒有任何問題的,可能是36的單臂路由支持的不是很好,我對網管的這個解釋unbelievable.
在坐車回來的路上,我一直在想着網管的解釋,想着36的單臂路由之間爲什麼路由會不通,怎麼想都覺得不可能,想着想着,突然想到,單臂路由中不是還配了native vlan嗎?配了native vlan的話不就得敲vlan dot1q tag native嗎?不敲就有可能不通的,尤其是在我敲試驗的機架上,不敲是絕對不通的,用的剛好也是36,於是推斷,問題的最大可能性,就是沒有敲這條命令導致native vlan的信息傳丟了網絡不通。
關於native vlan的這條命令到底是什麼,CISCO的官網給出的解釋是以下鏈接http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SXF/native/configuration/guide/dot1qtnl.html
對於脫機的朋友,我把原文粘貼如下:
1.Understanding How 802.1Q Tunneling Works
802.1Q tunneling enables service providers to use a single VLAN to support customers who have multiple VLANs, while preserving customer VLAN IDs and keeping traffic in different customer VLANs segregated.
A port configured to support 802.1Q tunneling is called a tunnel port. When you configure tunneling, you assign a tunnel port to a VLAN that you dedicate to tunneling, which then becomes a tunnel VLAN. To keep customer traffic segregated, each customer requires a separate tunnel VLAN, but that one tunnel VLAN supports all of the customer's VLANs.
802.1Q tunneling is not restricted to point-to-point tunnel configurations. Any tunnel port in a tunnel VLAN is a tunnel entry and exit point. An 802.1Q tunnel can have as many tunnel ports as are needed to connect customer switches.
The customer switches are trunk connected, but with 802.1Q tunneling, the service provider switches only use one service provider VLAN to carry all the customer VLANs, instead of directly carrying all the customer VLANs.
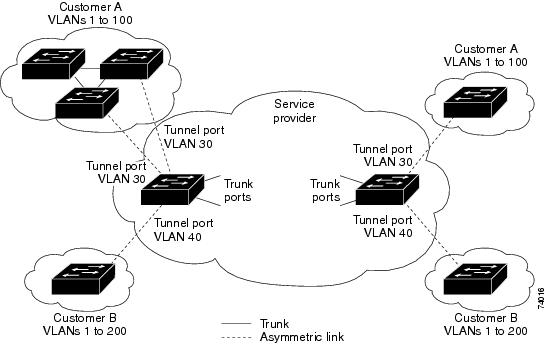
With 802.1Q tunneling, tagged customer traffic comes from an 802.1Q trunk port on a customer device and enters the service-provider edge switch through a tunnel port. The link between the 802.1Q trunk port on a customer device and the tunnel port is called an asymmetrical link because one end is configured as an 802.1Q trunk port and the other end is configured as a tunnel port. You assign the tunnel port to an access VLAN ID unique to each customer. See Figure 17-1 and Figure 17-2.
Figure 17-1 IEEE 802.1Q Tunnel Ports in a Service-Provider Network
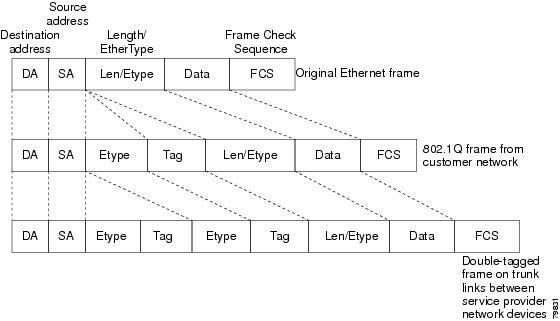
Figure 17-2 Untagged, 802.1Q-Tagged, and Double-Tagged Ethernet Frames
When a tunnel port receives tagged customer traffic from an 802.1Q trunk port, it does not strip the received 802.1Q tag from the frame header; instead, the tunnel port leaves the 802.1Q tag intact, adds a 2-byte Ethertype field (0x8100) followed by a 2-byte field containing the priority (CoS) and the VLAN. The received customer traffic is then put into the VLAN to which the tunnel port is assigned. This Ethertype 0x8100 traffic, with the received 802.1Q tag intact, is called tunnel traffic.
A VLAN carrying tunnel traffic is an 802.1Q tunnel. The tunnel ports in the VLAN are the tunnel's ingress and egress points.
The tunnel ports do not have to be on the same network device. The tunnel can cross other network links and other network devices before reaching the egress tunnel port. A tunnel can have as many tunnel ports as required to support the customer devices that need to communicate through the tunnel.
An egress tunnel port strips the 2-byte Ethertype field (0x8100) and the 2-byte length field and transmits the traffic with the 802.1Q tag still intact to an 802.1Q trunk port on a customer device. The 802.1Q trunk port on the customer device strips the 802.1Q tag and puts the traffic into the appropriate customer VLAN.
Note Tunnel traffic carries a second 802.1Q tag only when it is on a trunk link between service-provider network devices, with the outer tag containing the service-provider-assigned VLAN ID and the inner tag containing the customer-assigned VLAN IDs.
2.802.1Q Tunneling Configuration Guidelines and Restrictions
When configuring 802.1Q tunneling in your network, follow these guidelines and restrictions:
•Use asymmetrical links to put traffic into a tunnel or to remove traffic from a tunnel.
•Configure tunnel ports only to form an asymmetrical link.
•Dedicate one VLAN for each tunnel.
•Assign only tunnel ports to VLANs used for tunneling.
•Trunks require no special configuration to carry tunnel VLANs.
•Tunnel ports are not trunks. Any commands to configure trunking are inactive while the port is configured as a tunnel port.
•Tunnel ports learn customer MAC addresses.
•We recommend that you use ISL trunks to carry tunnel traffic between devices that do not have tunnel ports. Because of the 802.1Q native VLAN feature, using 802.1Q trunks requires that you be very careful when you configure tunneling: a mistake might direct tunnel traffic to a non-tunnel port.
•Ensure that the native VLAN of the 802.1Q trunk port in an asymmetrical link carries no traffic. Because traffic in the native VLAN is untagged, it cannot be tunneled correctly. Alternatively, you can enter the global vlan dot1q tag native command to tag native VLAN egress traffic and drop untagged native VLAN ingress traffic.
•Configure jumbo frame support on tunnel ports:
–See the "Configuring Jumbo Frame Support" section on page 9-10.
–Take note of the modules listed in the "Configuring Jumbo Frame Support" section that do not support jumbo frames.
•Jumbo frames can be tunneled as long as the jumbo frame length combined with the 802.1Q tag does not exceed the maximum frame size.
•Because tunnel traffic has the added ethertype and length field and retains the 802.1Q tag within the switch, the following restrictions exist:
–The Layer 3 packet within the Layer 2 frame cannot be identified in tunnel traffic.
–Layer 3 and higher parameters cannot be identified in tunnel traffic (for example, Layer 3 destination and source addresses).
–Because the Layer 3 addresses cannot be identified within the packet, tunnel traffic cannot be routed.
–The switch can provide only MAC-layer filtering for tunnel traffic (VLAN IDs and source and destination MAC addresses).
–The switch can provide only MAC-layer access control and QoS for tunnel traffic.
–QoS cannot detect the received CoS value in the 802.1Q 2-byte Tag Control Information field.
•On an asymmetrical link, the Cisco Discovery Protocol (CDP) reports a native VLAN mismatch if the VLAN of the tunnel port does not match the native VLAN of the 802.1Q trunk. The 802.1Q tunnel feature does not require that the VLANs match. Ignore the messages if your configuration requires nonmatching VLANs.
•Asymmetrical links do not support the Dynamic Trunking Protocol (DTP) because only one port on the link is a trunk. Configure the 802.1Q trunk port on an asymmetrical link to trunk unconditionally.
•The 802.1Q tunneling feature cannot be configured on ports configured to support private VLANs.
•The following Layer 2 protocols work between devices connected by an asymmetrical link:
–CDP
–UniDirectional Link Detection (UDLD)
–Port Aggregation Protocol (PAgP)
–Link Aggregation Control Protocol (LACP)
•PortFast BPDU filtering is enabled automatically on tunnel ports.
•CDP is automatically disabled on tunnel ports.
•VLAN Trunk Protocol (VTP) does not work between the following devices:
–Devices connected by an asymmetrical link
–Devices communicating through a tunnel
Note VTP works between tunneled devices if Layer 2 protocol tunneling is enabled. See Chapter 18, "Configuring Layer 2 Protocol Tunneling," for configuration details.
•To configure an EtherChannel as an asymmetrical link, all ports in the EtherChannel must have the same tunneling configuration. Because the Layer 3 packet within the Layer 2 frame cannot be identified, you must configure the EtherChannel to use MAC-address-based frame distribution.
The following configuration guidelines are required for your Layer 2 protocol tunneling configuration:
•On all the service provider edge switches, PortFast BPDU filtering must be enabled on the 802.1Q tunnel ports as follows:
Router(config-if)# spanning-tree bpdufilter enable
Router(config-if)# spanning-tree portfast
Note PortFast BPDU filtering is enabled automatically on tunnel ports.
•At least one VLAN must be available for Native VLAN tagging (vlan dot1q tag native option). If you use all the available VLANs and then try to enable the vlan dot1q tag native option, the option will not be enabled.
•On all the service provider core switches, tag native VLAN egress traffic and drop untagged native VLAN ingress traffic by entering the following command:
Router(config)# vlan dot1q tag native
•On all the customer switches, either enable or disable the global vlan dot1q tag native option.
Note If this option is enabled on one switch and disabled on another switch, all traffic is dropped; all customer switches must have this option configured the same on each switch.
The following configuration guidelines are optional for your Layer 2 protocol tunneling configuration:
•Because all the BPDUs are being dropped, spanning tree PortFast can be enabled on Layer 2 protocol tunnel ports as follows:
Router(config-if)# spanning-tree portfast trunk
•If the service provider does not want the customer to see its switches, CDP should be disabled on the 802.1Q tunnel port as follows:
Router(config-if)# no cdp enable
3.Configuring 802.1Q Tunneling
These sections describe 802.1Q tunneling configuration:
•Configuring 802.1Q Tunnel Ports
•Configuring the Switch to Tag Native VLAN Traffic
Caution Ensure that only the appropriate tunnel ports are in any VLAN used for tunneling and that one VLAN is used for each tunnel. Incorrect assignment of tunnel ports to VLANs can forward traffic inappropriately.
a)Configuring 802.1Q Tunnel Ports
To configure 802.1Q tunneling on a port, perform this task:
Command Purpose
Step 1 Router(config)# interface type1 slot/port Selects the LAN port to configure.
Step 2 Router(config-if)# switchport Configures the LAN port for Layer 2 switching:
•You must enter the switchport command once without any keywords to configure the LAN port as a Layer 2 interface before you can enter additional switchport commands with keywords.
•Required only if you have not entered the switchport command already for the interface.
Step 3 Router(config-if)# switchport mode dot1q-tunnel Configures the Layer 2 port as a tunnel port.
Router(config-if)# no switchport mode dot1q-tunnel Clears the tunnel port configuration.
Step 4 Router(config-if)# end Exits configuration mode.
Step 5 Router# show dot1q-tunnel [{interface type interface-number}] Verifies the configuration.
1 type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
This example shows how to configure tunneling on port 4/1 and verify the configuration:
Router# configure terminal
Router(config)# interface fastethernet 4/1
Router(config-if)# switchport mode dot1q-tunnel
Router(config-if)# end
Router# show dot1q-tunnel interface
b)Configuring the Switch to Tag Native VLAN Traffic
The vlan dot1q tag native command is a global command that configures the switch to tag native VLAN traffic, and admit only 802.1Q tagged frames on 802.1Q trunks, dropping any untagged traffic, including untagged traffic in the native VLAN.
To configure the switch to tag traffic in the native VLAN, perform this task:
Command Purpose
Step 1 Router(config)# vlan dot1q tag native Configures the switch to tag native VLAN traffic.
Router(config)# no vlan dot1q tag native Clears the configuration.
Step 2 Router(config)# end Exits configuration mode.
Step 3 Router# show vlan dot1q tag native Verifies the configuration.
This example shows how to configure the switch to tag native VLAN traffic and verify the configuration:
Router# configure terminal
Router(config)# vlan dot1q tag native
Router(config)# end
Router# show vlan dot1q tag native