實驗拓撲:
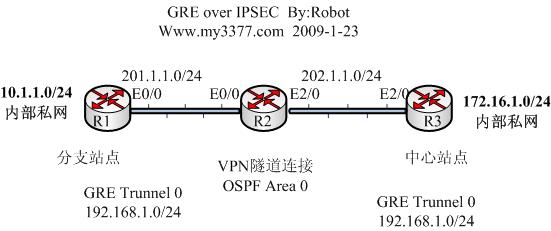
1:配置基本路由和需保護流量的感興趣訪問列表(注意這裏感興趣流 量設爲GRE隧道流量)
2:配置GRE Tunnel隧道.
3:配置IPSEC ×××.
4 :配置動態路由協議.
配置如下 :
R1#sho run
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 202.1.1.2
!
crypto ipsec transform-set mytrans esp-3des
!
crypto map mymap 1 ipsec-isakmp
set peer 202.1.1.2
set transform-set mytrans
match address 101
!
interface Loopback0
ip address 10.1.1.1 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
tunnel source Ethernet0/0
tunnel destination 202.1.1.2
!
interface Ethernet0/0
ip address 201.1.1.1 255.255.255.0
crypto map mymap
router ospf 1
log-adjacency-changes
network 10.1.1.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 Ethernet0/0
access-list 101 permit gre host 201.1.1.1 host 202.1.1.2
//注意訪問列表所定義的IPSEC所保護的感興趣流量爲GRE流量.
interface Ethernet0/0
ip address 201.1.1.2 255.255.255.0
!
interface Ethernet2/0
ip address 202.1.1.1 255.255.255.0
R3#
crypto isakmp policy 10
authentication pre-share
crypto isakmp key cisco address 201.1.1.1
!
!
crypto ipsec transform-set mytrans esp-3des
!
crypto map mymap 10 ipsec-isakmp
set peer 201.1.1.1
set transform-set mytrans
match address 101
!
interface Loopback0
ip address 172.16.1.1 255.255.255.0
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
tunnel source Ethernet2/0
tunnel destination 201.1.1.1
!
interface Ethernet2/0
ip address 202.1.1.2 255.255.255.0
half-duplex
crypto map mymap
!
router ospf 1
log-adjacency-changes
network 172.16.1.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
ip route 0.0.0.0 0.0.0.0 Ethernet2/0
!
access-list 101 permit gre host 202.1.1.2 host 201.1.1.1
R1#show ip os nei
172.16.1.1 0 FULL/ - 00:00:37 192.168.1.2 Tunnel0
R1#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
172.16.0.0/32 is subnetted, 1 subnets
O 172.16.1.1 [110/11112] via 192.168.1.2, 00:41:22, Tunnel0
10.0.0.0/24 is subnetted, 1 subnets
C 10.1.1.0 is directly connected, Loopback0
C 192.168.1.0/24 is directly connected, Tunnel0
S* 0.0.0.0/0 is directly connected, Ethernet0/0
R1#show crypto isakmp sa
dst src state conn-id slot
202.1.1.2 201.1.1.1 QM_IDLE 8 0
Tracing the route to 172.16.1.1
